Siemplify¶
Table of Contents¶
Release Notes¶
Version |
Date |
Notes |
|---|---|---|
1.0.1 |
07/2024 |
Converted workflows to Python3 |
1.0.0 |
02/2022 |
Initial Release |
Overview¶
Siemplify App for IBM QRadar SOAR
Bi-directional synchronization with Siemplify Cases, Entities, Attachments and Insights. Additional capabilities exist to list and add entries to the Siemplify Blocklist and Custom List.
Key Features¶
Sync QRadar SOAR incidents (including notes, artifacts, and attachments) with Siemplify cases
Sync Siemplify case close events with QRadar SOAR incidents
Sync Siemplify case changes with existing QRadar SOAR incidents
Flexible templates used allowing modification for your environment
Get entities added to the Block or Custom list
Add entities to the Block or Custom list
Add Playbooks to a Case
Requirements¶
This app supports the IBM Security QRadar SOAR Platform and the IBM Security QRadar SOAR for IBM Cloud Pak for Security.
SOAR platform¶
The SOAR platform supports two app deployment mechanisms, Edge Gateway (also known as App Host) and integration server.
If deploying to a SOAR platform with an App Host, the requirements are:
SOAR platform >=
51.0.0.0.9340.The app is in a container-based format (available from the AppExchange as a
zipfile).
If deploying to a SOAR platform with an integration server, the requirements are:
SOAR platform >=
51.0.0.0.9340.The app is in the older integration format (available from the AppExchange as a
zipfile which contains atar.gzfile).Integration server is running
resilient-circuits>=43.0.0.If using an API key account, make sure the account provides the following minimum permissions:
Name
Permissions
Org Data
Read
Function
Read
The following SOAR platform guides provide additional information:
Edge Gateway Deployment Guide or App Host Deployment Guide: provides installation, configuration, and troubleshooting information, including proxy server settings.
Integration Server Guide: provides installation, configuration, and troubleshooting information, including proxy server settings.
System Administrator Guide: provides the procedure to install, configure and deploy apps.
The above guides are available on the IBM Documentation website at ibm.biz/soar-docs. On this web page, select your SOAR platform version. On the follow-on page, you can find the Edge Gateway Deployment Guide, App Host Deployment Guide, or Integration Server Guide by expanding Apps in the Table of Contents pane. The System Administrator Guide is available by expanding System Administrator.
Cloud Pak for Security¶
If you are deploying to IBM Cloud Pak for Security, the requirements are:
IBM Cloud Pak for Security >=
1.10.15.Cloud Pak is configured with an Edge Gateway.
The app is in a container-based format (available from the AppExchange as a
zipfile).
The following Cloud Pak guides provide additional information:
Edge Gateway Deployment Guide or App Host Deployment Guide: provides installation, configuration, and troubleshooting information, including proxy server settings. From the Table of Contents, select Case Management and Orchestration & Automation > Orchestration and Automation Apps.
System Administrator Guide: provides information to install, configure, and deploy apps. From the IBM Cloud Pak for Security IBM Documentation table of contents, select Case Management and Orchestration & Automation > System administrator.
These guides are available on the IBM Documentation website at ibm.biz/cp4s-docs. From this web page, select your IBM Cloud Pak for Security version. From the version-specific IBM Documentation page, select Case Management and Orchestration & Automation.
Proxy Server¶
The app does support a proxy server.
Python Environment¶
Python 3.9, 3.11, and 3.12 are officially supported. When deployed as an app, the app runs on Python 3.11. Additional package dependencies may exist for each of these packages:
jinja2
pytz
resilient-circuits>=43.0.0
retry2 ~= 0.9
simplejson
Development Version¶
This app has been implemented using:
Product Name |
Product Version |
API URL |
API Version |
|---|---|---|---|
Siemplify |
5.6.x |
https://<siemplify_host>/api/external/v1 |
v1 |
Configuration¶
Generate an Siemplify API Key for use with IBM SOAR. This value will used with the app.config
api_keysetting.
Installation¶
Install¶
To install or uninstall an App or Integration on the SOAR platform, see the documentation at ibm.biz/soar-docs.
To install or uninstall an App on IBM Cloud Pak for Security, see the documentation at ibm.biz/cp4s-docs and follow the instructions above to navigate to Orchestration and Automation.
App Configuration¶
The following table provides the settings you need to configure the app. These settings are made in the app.config file. See the documentation discussed in the Requirements section for the procedure.
Config |
Required |
Example |
Description |
|---|---|---|---|
base_url |
Yes |
|
Base URL for your Siemplify server |
api_key |
Yes |
|
API Generated from Siemplify |
cafile |
Yes |
`false |
/path/to/siemplify.cert` |
polling_interval |
No |
|
Seconds to wait between polling intervals. 0 disables poller. This will disable the ability to close an IBM QRadar SOAR incient when the Siempify Case closes. |
polling_lookback |
No |
|
Minutes to look back for cased cases the first time poller runs |
poller_timezone |
No |
|
Timezone adjustment for Siemplify timestamp comparison |
default_environment |
No |
|
Siemplify environment to use when creating cases and entities if none specifically referenced |
siemplify_create_case_template |
No |
|
Use when overriding the default template |
soar_close_case_template |
No |
|
Use when overriding the default template |
soar_update_case_template |
No |
|
Use when overriding the default template |
artifact_type_lookup |
No |
|
Use to specify an override JSON file with a mapping between QRadar SOAR artifact types and Siemplify entities |
playbook_mappings |
No |
|
* Lookup key/value pairs to mapp a QRadar SOAR incident type to Siemplify playbook(s)* |
Function - Siemplify Add Playbook¶
Add a playbook to a Siemplify Case
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
Siemplify alert id saved in the SOAR incident |
|
|
Yes |
|
Siemplify case id saved in the SOAR incident |
|
|
Yes |
|
Name of Playbook to add |
|
|
Yes |
`True |
False` |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"success": false
},
"inputs": {
"siemplify_alert_id": "IBM SOAR Alert 3834_64215769-ecb2-4fd7-bfb9-e6ca81c7a869",
"siemplify_case_id": 171,
"siemplify_playbook_name": "SentinelOne Threat Remediation",
"siemplify_run_playbook_automatically": true
},
"metrics": {
"execution_time_ms": 312,
"host": "localhost",
"package": "fn-siemplify",
"package_version": "1.0.0",
"timestamp": "2022-03-31 17:31:39",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.siemplify_alert_id = incident.properties.siemplify_alert_id
inputs.siemplify_case_id = incident.properties.siemplify_case_id
inputs.siemplify_playbook_name = rule.properties.siemplify_playbook_name
inputs.siemplify_run_playbook_automatically = rule.properties.siemplify_run_playbook_automatically
Example Function Post Process Script:
if results.success:
incident.addNote("Siemplify Add Playbook: '{}' created".format(rule.properties.siemplify_playbook_name))
else:
incident.addNote("Siemplify Add Playbook: '{}' failed: ".format(rule.properties.siemplify_playbook_name, results.reason))
Function - Siemplify Add/Update Entity to Custom List¶
Add an artifact to the Siemplify custom list
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
No |
|
- |
|
|
No |
|
- |
|
|
No |
|
If left empty, the artifact type is used |
|
|
No |
|
Set environment. See app.config setting for default |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"category": "SOAR",
"entityIdentifier": "194.34.44.53",
"environments": [
"Default Environment"
]
},
"inputs": {
"siemplify_artifact_type": "IP Address",
"siemplify_artifact_value": "194.34.44.53",
"siemplify_category": "SOAR",
"siemplify_environment": "Default Environment"
},
"metrics": {
"execution_time_ms": 298,
"host": "localhost",
"package": "fn-siemplify",
"package_version": "1.0.0",
"timestamp": "2022-03-31 18:45:48",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.siemplify_artifact_type = artifact.type
inputs.siemplify_artifact_value = artifact.value
inputs.siemplify_category = rule.properties.siemplify_list_category
inputs.siemplify_environment = rule.properties.siemplify_environments
Example Function Post Process Script:
from datetime import datetime
current_dt = datetime.now()
if results.success:
entity = results.content
row = incident.addRow('siemplify_list_entries')
row['report_date'] = current_dt
row['list_name'] = 'Custom List'
row['entity'] = entity['entityIdentifier']
row['entity_type'] = entity['category']
row['environments'] = ", ".join(entity['environments'])
incident.addNote("Siemplify Add/Update Custom List successful for: {} ({})".format(artifact.value, artifact.type))
else:
incident.addNote("Siemplify Add/Update Custom List Entity failed: {}".format(results.reason))
Function - Siemplify Close Case¶
Close a Siemplify Case
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
Siemplify alert id saved in the SOAR incident |
|
|
Yes |
|
Siemplify case id saved in the SOAR incident |
|
|
No |
|
Added as the Siemplfy close comment |
|
|
Yes |
|
Added as the Siemplify close reason |
|
|
Yes |
|
Added as the Siemplify root cause |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"close_case": true
},
"inputs": {
"siemplify_alert_id": "IBM SOAR Alert 3860_7f3e3ad8-4749-4040-a49d-c09beb673a5e",
"siemplify_case_id": 196,
"siemplify_reason": "Inconclusive",
"siemplify_root_cause": "\u003cdiv class=\"rte\"\u003e\u003cdiv\u003enot an issue\u003c/div\u003e\u003c/div\u003e"
},
"metrics": {
"execution_time_ms": 791,
"host": "localhost",
"package": "fn-siemplify",
"package_version": "1.0.0",
"timestamp": "2022-03-31 18:47:16",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
# change as necessary. Value Siemplify values are: Malicious, Non Malicious, Maintenance, Inconclusive
LOOKUP_STATUS = {
"7": "Inconclusive", # Unresolved
"8": "Inconclusive", # Duplicate
"9": "Non Malicious", # Not an Issue
"10": "Malicious" # Resolved
}
inputs.siemplify_alert_id = incident.properties.siemplify_alert_id
inputs.siemplify_case_id = incident.properties.siemplify_case_id
inputs.siemplify_root_cause = incident.resolution_summary.content
inputs.siemplify_reason = LOOKUP_STATUS.get(str(incident.resolution_id), 'Inconclusive')
Example Function Post Process Script:
if results.success:
note = "Siemplify Sync cased {} closed".format(incident.properties.siemplify_case_id)
else:
note = "Siemplify Sync cased {} failed to close: {}".format(incident.properties.siemplify_case_id, results.reason)
incident.addNote(helper.createPlainText(note))
Function - Siemplify Get Custom List Entities¶
Get entities from Siemplify’s custom list
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
No |
|
Limit the results returned |
|
|
No |
|
Filter results based on a search entry |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": [
{
"category": "soar_category",
"creationTimeUnixTimeInMs": 1638827701814,
"entityIdentifier": "soar_list",
"environments": [
"Default Environment"
],
"forDBMigration": false,
"id": 1,
"modificationTimeUnixTimeInMs": 1638827701814
},
{
"category": "soar_category",
"creationTimeUnixTimeInMs": 1641490099338,
"entityIdentifier": "soar2_list",
"environments": [
"Default Environment"
],
"forDBMigration": false,
"id": 2,
"modificationTimeUnixTimeInMs": 1641490099338
},
{
"category": "aa",
"creationTimeUnixTimeInMs": 1641507308926,
"entityIdentifier": "soar3_list",
"environments": [
"Default Environment"
],
"forDBMigration": false,
"id": 3,
"modificationTimeUnixTimeInMs": 1641507308926
},
{
"category": "soar_category",
"creationTimeUnixTimeInMs": 1641511563361,
"entityIdentifier": "123",
"environments": [
"Default Environment"
],
"forDBMigration": false,
"id": 4,
"modificationTimeUnixTimeInMs": 1641511563361
},
{
"category": "new category",
"creationTimeUnixTimeInMs": 1641515897058,
"entityIdentifier": "def.com",
"environments": [
"Default Environment"
],
"forDBMigration": false,
"id": 5,
"modificationTimeUnixTimeInMs": 1641515897058
},
{
"category": "new category",
"creationTimeUnixTimeInMs": 1641516046817,
"entityIdentifier": "service",
"environments": [
"Default Environment"
],
"forDBMigration": false,
"id": 6,
"modificationTimeUnixTimeInMs": 1641516046817
},
{
"category": "new category",
"creationTimeUnixTimeInMs": 1641516166266,
"entityIdentifier": "something",
"environments": [
"Default Environment"
],
"forDBMigration": false,
"id": 7,
"modificationTimeUnixTimeInMs": 1641516166266
},
{
"category": "Malicious Category",
"creationTimeUnixTimeInMs": 1641572735756,
"entityIdentifier": "malicious.exe",
"environments": [
"Default Environment"
],
"forDBMigration": false,
"id": 8,
"modificationTimeUnixTimeInMs": 1641572735756
},
{
"category": "USERUNIQNAME",
"creationTimeUnixTimeInMs": 1641584158260,
"entityIdentifier": "abc@example.com",
"environments": [
"Default Environment"
],
"forDBMigration": false,
"id": 9,
"modificationTimeUnixTimeInMs": 1641584158260
},
{
"category": "SOAR",
"creationTimeUnixTimeInMs": 1648766753651,
"entityIdentifier": "194.34.44.53",
"environments": [
"Default Environment"
],
"forDBMigration": false,
"id": 12,
"modificationTimeUnixTimeInMs": 1648766753651
}
],
"inputs": {
"siemplify_environments": null,
"siemplify_limit": null
},
"metrics": {
"execution_time_ms": 271,
"host": "localhost",
"package": "fn-siemplify",
"package_version": "1.0.0",
"timestamp": "2022-03-31 18:46:36",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.siemplify_limit = rule.properties.siemplify_limit_result if rule.properties.siemplify_limit_result else None
inputs.siemplify_environments = rule.properties.siemplify_environments
Example Function Post Process Script:
from datetime import datetime
current_dt = datetime.now()
if results.success:
if isinstance(results.content, list):
entity_list = results.content
else:
entity_list = results.content.get("objectsList", {})
for entity in entity_list:
row = incident.addRow('siemplify_list_entries')
row['report_date'] = current_dt
row['list_name'] = 'Custom List'
row['entity'] = entity['entityIdentifier']
row['entity_type'] = entity['category']
row['environments'] = ", ".join(entity['environments'])
row['entity_id'] = entity['id']
else:
incident.addNote("Siemplify Get Custom List Entities failed: {}".format(results.reason))
Function - Siemplify Remove List Entry¶
Remove a Blocklist or Custom List entry
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
ID within the list |
|
|
Yes |
|
Name of blocklist or custom list |
|
|
Yes |
|
Type of the entity |
|
|
Yes |
|
Value of the entity |
|
|
Yes |
|
Environments |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": "",
"inputs": {
"siemplify_entity_id": 14,
"siemplify_entity_list": "Block List",
"siemplify_entity_type": "IPSET",
"siemplify_entity_value": "194.34.44.53",
"siemplify_environments": "Default Environment"
},
"metrics": {
"execution_time_ms": 279,
"host": "local",
"package": "fn-siemplify",
"package_version": "1.0.0",
"timestamp": "2022-05-03 21:22:42",
"version": "1.0"
},
"raw": "None",
"reason": "None",
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.siemplify_entity_id = row['entity_id']
inputs.siemplify_entity_list = row['list_name']
inputs.siemplify_entity_value = row['entity']
inputs.siemplify_entity_type = row['entity_type']
inputs.siemplify_environments = row['environments']
Example Function Post Process Script:
if results.success:
incident.addNote("Siemplify Remove {} Entity '{}' successful".format(row['list_name'], row['entity']))
row['entity'] = "{} (deleted)".format(row['entity'])
else:
incident.addNote("Siemplify Remove {} Entity '{}' failed: {}".format(row['list_name'], row['entity'], results.reason))
Function - Siemplify Sync Artifact¶
Sync a SOAR Incident artifact to a Siemplify CASE alert and entity
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
No |
|
Siemplify alert id saved in the SOAR incident |
|
|
Yes |
|
- |
|
|
Yes |
|
- |
|
|
Yes |
|
- |
|
|
No |
|
Siemplify case id saved in the SOAR incident |
|
|
No |
|
Set environment. See app.config setting for default |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {},
"inputs": {
"siemplify_alert_id": "IBM SOAR Alert 3860_7f3e3ad8-4749-4040-a49d-c09beb673a5e",
"siemplify_artifact_id": 7657,
"siemplify_artifact_type": "IP Address",
"siemplify_artifact_value": "194.34.44.53",
"siemplify_case_id": 196,
"siemplify_environment": null
},
"metrics": {
"execution_time_ms": 1322,
"host": "localhost",
"package": "fn-siemplify",
"package_version": "1.0.0",
"timestamp": "2022-03-31 18:43:53",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.siemplify_case_id = incident.properties.siemplify_case_id
inputs.siemplify_alert_id = incident.properties.siemplify_alert_id
inputs.siemplify_artifact_type = artifact.type
inputs.siemplify_artifact_value = artifact.value
inputs.siemplify_environment = None
inputs.siemplify_artifact_id = artifact.id
Example Function Post Process Script:
if results.success:
incident.addNote("Siemplify Sync Artifact: {} ({}) created".format(artifact.value, artifact.type))
else:
incident.addNote("Siemplify Sync Artifact: {} ({}) failed".format(artifact.value, artifact.type))
Function - Siemplify Sync Attachment¶
Create a Siemplify Attachment from a SOAR Case Attachment
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
Siemplify alert id saved in the SOAR incident |
|
|
Yes |
`` |
SOAR incident attachment id |
|
|
Yes |
|
Siemplify case id saved in the SOAR incident |
|
|
Yes |
|
SOAR incident id |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"alertIdentifier": null,
"caseId": 197,
"creationTimeUnixTimeInMs": 1648766978004,
"creatorUserId": "Siemplify automation",
"description": "Created by IBM SOAR",
"evidenceId": 25,
"evidenceName": "resilient-44.0.1.tar",
"evidenceThumbnailBase64": "",
"fileType": ".gz",
"id": 25,
"isFavorite": false,
"modificationTimeUnixTimeInMs": 1648766978004,
"type": 4
},
"inputs": {
"siemplify_alert_id": "IBM SOAR Alert 3861_eb6723b9-0ab7-4089-814a-1bc9748133eb",
"siemplify_attachment_id": 234,
"siemplify_case_id": 197,
"siemplify_incident_id": 3861
},
"metrics": {
"execution_time_ms": 935,
"host": "localhost",
"package": "fn-siemplify",
"package_version": "1.0.0",
"timestamp": "2022-03-31 18:49:33",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.siemplify_alert_id = incident.properties.siemplify_alert_id
inputs.siemplify_case_id = incident.properties.siemplify_case_id
inputs.siemplify_incident_id = incident.id
inputs.siemplify_attachment_id = attachment.id
Example Function Post Process Script:
if results.success:
incident.addNote("Siemplify Sync Attachment: {} created".format(attachment.name))
else:
incident.addNote("Siemplify Sync Attachment: {} failed. Reason: {}".format(attachment.name, results.reason))
Function - Siemplify Sync Case¶
Sync a SOAR Case to Siemplify
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
Siemplify alert id saved in the SOAR incident |
|
|
No |
|
Set Assigned User. Default is none. |
|
|
Yes |
|
Siemplify case id saved in the SOAR incident |
|
|
No |
|
Set environment. See app.config setting for default |
|
|
Yes |
|
SOAR incident Id |
|
|
No |
`true |
false` |
|
|
No |
`true |
false` |
|
|
No |
`true |
false` |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"additionalProperties": {},
"alerts": [
{
"additionalProperties": {
"alertGroupIdentifier": "Manual Case_3a649db8-8168-4c10-8925-ae3aa3d9307f",
"alertName": "IBM SOAR Alert 3861",
"detectionTime": "1648766937000",
"endTime": "1648766937000",
"identifier": "IBM SOAR Alert 3861_eb6723b9-0ab7-4089-814a-1bc9748133eb",
"isManualAlert": "True",
"priority": "Unchanged",
"ruleGenerator": "Manual Case",
"startTime": "1648766937000"
},
"apiSlaExpiration": {
"criticalExpirationTime": null,
"expirationStatus": 2,
"slaExpirationTime": null
},
"creationTimeUnixTimeInMs": 0,
"entityCards": [],
"fields": [
{
"groupName": "HIGHLIGHTED FIELDS",
"isHighlight": true,
"items": [
{
"name": "Alert Name",
"originalName": "AlertName",
"value": "IBM SOAR Alert 3861"
},
{
"name": "End Time",
"originalName": "EndTime",
"value": "1648766937000"
},
{
"name": "Start Time",
"originalName": "StartTime",
"value": "1648766937000"
}
]
},
{
"groupName": "Time",
"isHighlight": false,
"items": [
{
"name": "Detection Time",
"originalName": "DetectionTime",
"value": "1648766937000"
},
{
"name": "End Time",
"originalName": "EndTime",
"value": "1648766937000"
},
{
"name": "Start Time",
"originalName": "StartTime",
"value": "1648766937000"
}
]
},
{
"groupName": "Case",
"isHighlight": false,
"items": [
{
"name": "Alert Name",
"originalName": "AlertName",
"value": "IBM SOAR Alert 3861"
},
{
"name": "Rule Generator",
"originalName": "RuleGenerator",
"value": "Manual Case"
}
]
},
{
"groupName": "Default",
"isHighlight": false,
"items": [
{
"name": "AlertGroupIdentifier",
"originalName": "AlertGroupIdentifier",
"value": "Manual Case_3a649db8-8168-4c10-8925-ae3aa3d9307f"
},
{
"name": "IsManualAlert",
"originalName": "IsManualAlert",
"value": "True"
}
]
},
{
"groupName": "Threat",
"isHighlight": false,
"items": [
{
"name": "Priority",
"originalName": "Priority",
"value": "Unchanged"
}
]
}
],
"hasWorkflows": false,
"id": 0,
"identifier": "IBM SOAR Alert 3861_eb6723b9-0ab7-4089-814a-1bc9748133eb",
"isManualAlert": true,
"modificationTimeUnixTimeInMs": 0,
"name": "IBM SOAR Alert 3861",
"priority": 0,
"product": null,
"productFamilies": [
"Default"
],
"securityEventCards": [
{
"alertIdentifier": "IBM SOAR Alert 3861_eb6723b9-0ab7-4089-814a-1bc9748133eb",
"artificats": [],
"caseId": 197,
"destinations": [],
"deviceEventClassId": null,
"eventId": null,
"eventName": null,
"fields": [],
"outcome": null,
"port": null,
"product": null,
"sources": [],
"time": "2022-03-31T22:48:57Z"
}
],
"sourceSystemName": "",
"startTimeUnixTimeInMs": 1648766937000,
"ticketId": "",
"workflowsStatus": 2
}
],
"apiSlaExpiration": {
"criticalExpirationTime": null,
"expirationStatus": 2,
"slaExpirationTime": null
},
"apiStageSlaExpiration": {
"criticalExpirationTime": null,
"expirationStatus": 2,
"slaExpirationTime": null
},
"assignedUserName": "@Tier1",
"canOpenIncident": false,
"caseRecommendations": {
"relevantAnalysts": [],
"relevantTags": [],
"similarCases": [
{
"caseRecommendationOutcomeStatus": 0,
"closedComment": null,
"closedRootCause": null,
"creationTime": "2022-03-31T20:43:24.799Z",
"id": 167,
"isClosed": false,
"priority": "50",
"scorePercent": 100,
"title": "IBM SOAR - ReaQta Alert - Detection Strategy, Endpoint: REQTA-WINDOWS20"
},
{
"caseRecommendationOutcomeStatus": 0,
"closedComment": null,
"closedRootCause": null,
"creationTime": "2022-03-31T21:02:23.878Z",
"id": 192,
"isClosed": false,
"priority": "50",
"scorePercent": 100,
"title": "IBM SOAR - ReaQta Alert - Code Injection, Endpoint: HOST-9"
},
{
"caseRecommendationOutcomeStatus": 0,
"closedComment": null,
"closedRootCause": null,
"creationTime": "2022-03-31T20:43:28.91Z",
"id": 169,
"isClosed": false,
"priority": "50",
"scorePercent": 100,
"title": "IBM SOAR - ReaQta Alert - Code Injection, Endpoint: CHUCK-SURFACE-B"
},
{
"caseRecommendationOutcomeStatus": 0,
"closedComment": null,
"closedRootCause": null,
"creationTime": "2022-03-31T20:49:33.825Z",
"id": 171,
"isClosed": false,
"priority": "50",
"scorePercent": 100,
"title": "IBM SOAR - ReaQta Alert - Detection Strategy, Endpoint: DESKTOP-DJL"
},
{
"caseRecommendationOutcomeStatus": 4,
"closedComment": "Case closed by Siemplify API. All attached playbooks and playbook blocks have been terminated.",
"closedRootCause": "not an issue",
"creationTime": "2022-03-31T22:43:23.87Z",
"id": 196,
"isClosed": true,
"priority": "50",
"scorePercent": 100,
"title": "IBM SOAR - demonstration synchronization to siemplify"
}
]
},
"caseSource": "User",
"creationTimeUnixTimeInMs": 1648766970800,
"description": "some description",
"entities": [],
"entityCards": [],
"environment": "Default Environment",
"hasIncident": false,
"hasSuspiciousEntity": false,
"hasWorkflow": false,
"id": 197,
"insights": [],
"isImportant": true,
"isIncident": false,
"isMerged": false,
"isOverflowCase": false,
"isTestCase": false,
"isTouched": false,
"modificationTimeUnixTimeInMs": 1648766971895,
"priority": 50,
"productFamilies": [],
"siemplify_case_url": "https://9.55.194.8/#/main/cases/classic-view/197",
"stage": "Triage",
"status": 1,
"summary": {
"fields": []
},
"tags": [
{
"caseId": 197,
"priority": 0,
"tag": "IBMSOAR"
},
{
"caseId": 197,
"priority": 0,
"tag": "Manual Case"
}
],
"title": "IBM SOAR - Demo Synchronization to Siemplify",
"wallData": [
{
"alertIdentifier": "IBM SOAR Alert 3861_eb6723b9-0ab7-4089-814a-1bc9748133eb",
"caseId": 197,
"comment": "Case creation reason: IBM SOAR Incident 3861",
"creationTimeUnixTimeInMs": 1648766971173,
"creatorUserId": "Siemplify automation",
"id": 197,
"isFavorite": false,
"modificationTimeUnixTimeInMs": 1648766971173,
"type": 7
},
{
"activityKind": 6,
"alertIdentifier": null,
"caseId": 197,
"creationTimeUnixTimeInMs": 1648766971895,
"creatorUserId": "Siemplify automation",
"description": "\u200cDescription some description added to case",
"id": 286,
"isFavorite": false,
"modificationTimeUnixTimeInMs": 1648766971895,
"newValue": "some description",
"type": 1
},
{
"activityKind": 15,
"alertIdentifier": null,
"caseId": 197,
"creationTimeUnixTimeInMs": 1648766971394,
"creatorUserId": "Siemplify automation",
"description": "Tag \u0027Manual Case\u0027 added",
"id": 285,
"isFavorite": false,
"modificationTimeUnixTimeInMs": 1648766971394,
"newValue": "Manual Case",
"type": 1
},
{
"activityKind": 10,
"alertIdentifier": null,
"caseId": 197,
"creationTimeUnixTimeInMs": 1648766970821,
"creatorUserId": "System",
"description": "Case stage set to Triage",
"id": 198,
"isFavorite": false,
"modificationTimeUnixTimeInMs": 1648766970821,
"newValue": null,
"type": 1
}
]
},
"inputs": {
"siemplify_alert_id": null,
"siemplify_assigned_user": null,
"siemplify_case_id": null,
"siemplify_environment": null,
"siemplify_incident_id": 3861,
"siemplify_sync_artifacts": true,
"siemplify_sync_attachments": true,
"siemplify_sync_comments": true
},
"metrics": {
"execution_time_ms": 2400,
"host": "localhost",
"package": "fn-siemplify",
"package_version": "1.0.0",
"timestamp": "2022-03-31 18:49:27",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.siemplify_incident_id = incident.id
inputs.siemplify_assigned_user = None
inputs.siemplify_environment = None
inputs.siemplify_case_id = incident.properties.siemplify_case_id
inputs.siemplify_alert_id = incident.properties.siemplify_alert_id
Example Function Post Process Script:
PRIORITY_LOOKUP = {-1: "Informational", 40: "Low", 50:"Medium", 60:"Medium", 80:"High", 100:"Critical", "DEFAULT": "Medium"}
if results.success:
case = results.content
incident.properties.siemplify_case_id = case.get('id')
incident.properties.siemplify_case_link = helper.createRichText("<a target='blank' href='{}'>{}</a>".format(case.get('siemplify_case_url'), case.get('title')))
incident.properties.siemplify_is_important = case.get('isImportant')
incident.properties.siemplify_stage = case.get('stage')
incident.properties.siemplify_assignee = case.get('assignedUserName')
incident.properties.siemplify_priority = PRIORITY_LOOKUP.get(case.get('priority'), str(case.get('priority')))
incident.properties.siemplify_tags = ", ".join([tag['tag'] for tag in case.get('tags')])
if results.content.get('alerts'):
incident.properties.siemplify_alert_id = case['alerts'][0]['identifier']
incident.addNote("Siemplify Sync Case {} created".format(case.get('id')))
else:
incident.addNote("Siemplify Sync Case failed: {}".format(str(results.content)))
Function - Siemplify Sync Comment¶
Create a Siemplify Case comment
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
No |
|
Siemplify alert id saved in the SOAR incident |
|
|
No |
|
Siemplfy case id saved in the SOAR incident |
|
|
No |
|
- |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"ErrorCode": 2000,
"ErrorMessage": "This insight already exists.",
"InnerException": null,
"InnerExceptionType": null
},
"inputs": {
"siemplify_alert_id": "IBM SOAR Alert 3842_48c9cb33-0047-4e6d-b799-dc765d0e5e68",
"siemplify_case_id": 179,
"siemplify_comment": "ReaQta Create Artifact failed: ReaQta Error: \n status code: 422\n message: Endpoint offline\n details: {\u0027endpointId\u0027: \u0027847075616325894144\u0027, \u0027lastSeenAt\u0027: \u00272022-03-29T19:09:45.373Z\u0027}"
},
"metrics": {
"execution_time_ms": 264,
"host": "localhost",
"package": "fn-siemplify",
"package_version": "1.0.0",
"timestamp": "2022-03-31 17:02:28",
"version": "1.0"
},
"raw": null,
"reason": "Siemplify Error: \n status code: 500\n failure: This insight already exists.",
"success": false,
"version": 2.0
}
Example Function Input Script:
inputs.siemplify_alert_id = incident.properties.siemplify_alert_id
inputs.siemplify_case_id = incident.properties.siemplify_case_id
inputs.siemplify_comment = note.text.content
Example Function Post Process Script:
if results.success:
note.text = "<b>Siemplify Sync complete</b><br>"+note.text.content
else:
incident.addNote(helper.createRichText("Siemplify Sync for note failed. Reason: {}".format(results.reason)))
Function - Siemplify Sync Task¶
Sync a SOAR Task to Siemplify
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
No |
|
Siemplify case Id stored with the SOAR incident |
|
|
No |
|
SOAR incident task id |
|
|
No |
|
Name of Siemplify assignee for the task |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"alertIdentifier": null,
"caseId": 196,
"completionComment": null,
"completionDateTimeUnixTimeInMs": null,
"completor": null,
"creationTimeUnixTimeInMs": 1648766815969,
"creatorUserId": "Siemplify automation",
"dueDateUnixTimeInMs": null,
"id": 24,
"isFavorite": false,
"modificationTimeUnixTimeInMs": 1648766815969,
"name": "IBM SOAR: Investigate Exposure of Personal Information/Data",
"owner": "@Administrator",
"priority": 0,
"status": 0,
"type": 2
},
"inputs": {
"siemplify_case_id": 196,
"siemplify_soar_task_id": 2853,
"siemplify_task_assignee": "@Administrator"
},
"metrics": {
"execution_time_ms": 447,
"host": "localhost",
"package": "fn-siemplify",
"package_version": "1.0.0",
"timestamp": "2022-03-31 18:46:51",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.siemplify_case_id = incident.properties.siemplify_case_id
inputs.siemplify_soar_task_id = task.id
inputs.siemplify_task_assignee = "@Administrator"
Example Function Post Process Script:
if results.success:
task.addNote("Siemplify Sync Task: {}".format(task.name))
else:
task.addNote("Siemplify Sync Task: {} failed: {}".format(task.name, results.reason))
Function - Siemplify: Add/Update Entity to Blocklist¶
Add an artifact to the Siemplify Blacklist
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
No |
|
- |
|
|
No |
|
- |
|
|
No |
|
Set environment. See app.config setting for default |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"entityIdentifier": "194.34.44.53",
"entityType": "IPSET",
"environments": [
"Default Environment"
],
"scope": 2
},
"inputs": {
"siemplify_artifact_type": "IP Address",
"siemplify_artifact_value": "194.34.44.53",
"siemplify_environment": "Default Environment"
},
"metrics": {
"execution_time_ms": 279,
"host": "localhost",
"package": "fn-siemplify",
"package_version": "1.0.0",
"timestamp": "2022-03-31 18:45:26",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.siemplify_artifact_type = artifact.type
inputs.siemplify_artifact_value = artifact.value
inputs.siemplify_environment = rule.properties.siemplify_environments
Example Function Post Process Script:
from datetime import datetime
current_dt = datetime.now()
if results.success:
entity = results.content
row = incident.addRow('siemplify_list_entries')
row['report_date'] = current_dt
row['list_name'] = 'Block List'
row['entity'] = entity['entityIdentifier']
row['entity_type'] = entity['entityType']
row['environments'] = ", ".join(entity['environments'])
incident.addNote("Siemplify Add/Update Blocklist successful for: {} ({})".format(artifact.value, artifact.type))
else:
incident.addNote("Siemplify Add/Update Blocklist Entity failed: {}".format(results.reason))
Function - Siemplify: Get Blocklist Entities¶
Get entities from Siemplify’s Blacklist
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
No |
|
Limit the results returned |
|
|
No |
|
Filter results based on a search entry |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": [
{
"elementType": 0,
"entityIdentifier": "https://abc.com",
"entityType": "DestinationURL",
"environments": [
"Default Environment"
],
"id": 1,
"scope": 2
},
{
"elementType": 0,
"entityIdentifier": "1.2.3.4",
"entityType": "IPSET",
"environments": [
"Default Environment"
],
"id": 2,
"scope": 2
},
{
"elementType": 0,
"entityIdentifier": "5.6.7.8",
"entityType": "IPSET",
"environments": [
"Default Environment"
],
"id": 3,
"scope": 2
},
{
"elementType": 0,
"entityIdentifier": "a@example.com",
"entityType": "USERUNIQNAME",
"environments": [
"Default Environment"
],
"id": 4,
"scope": 2
},
{
"elementType": 0,
"entityIdentifier": "aaa.exe",
"entityType": "PROCESS",
"environments": [
"Default Environment"
],
"id": 5,
"scope": 2
},
{
"elementType": 0,
"entityIdentifier": "malicious.exe",
"entityType": "FILENAME",
"environments": [
"Default Environment"
],
"id": 6,
"scope": 2
},
{
"elementType": 0,
"entityIdentifier": "abc@example.com",
"entityType": "USERUNIQNAME",
"environments": [
"Default Environment"
],
"id": 7,
"scope": 2
},
{
"elementType": 0,
"entityIdentifier": "dns.com",
"entityType": "DESTINATIONDOMAIN",
"environments": [
"Default Environment"
],
"id": 11,
"scope": 2
},
{
"elementType": 0,
"entityIdentifier": "demo.com",
"entityType": "DESTINATIONDOMAIN",
"environments": [
"Default Environment"
],
"id": 12,
"scope": 2
},
{
"elementType": 0,
"entityIdentifier": "139.28.235.26",
"entityType": "IPSET",
"environments": [
"Default Environment"
],
"id": 13,
"scope": 2
},
{
"elementType": 0,
"entityIdentifier": "194.34.44.53",
"entityType": "IPSET",
"environments": [
"Default Environment"
],
"id": 14,
"scope": 2
}
],
"inputs": {
"siemplify_limit": 100,
"siemplify_search": null
},
"metrics": {
"execution_time_ms": 333,
"host": "localhost",
"package": "fn-siemplify",
"package_version": "1.0.0",
"timestamp": "2022-03-31 18:46:31",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.siemplify_limit = rule.properties.siemplify_limit_result if rule.properties.siemplify_limit_result else 100
inputs.siemplify_search = rule.properties.siemplify_search_term
Example Function Post Process Script:
from datetime import datetime
current_dt = datetime.now()
if results.success:
if isinstance(results.content, list):
entity_list = results.content
else:
entity_list = results.content.get("objectsList", {})
for entity in entity_list:
row = incident.addRow('siemplify_list_entries')
row['report_date'] = current_dt
row['list_name'] = 'Block List'
row['entity'] = entity['entityIdentifier']
row['entity_type'] = entity['entityType']
row['environments'] = ", ".join(entity['environments'])
row['entity_id'] = entity['id']
else:
incident.addNote("Siemplify Get Blocklist Entities failed: {}".format(results.reason))
Custom Layouts¶
Import the Data Tables and Custom Fields like the screenshot below:
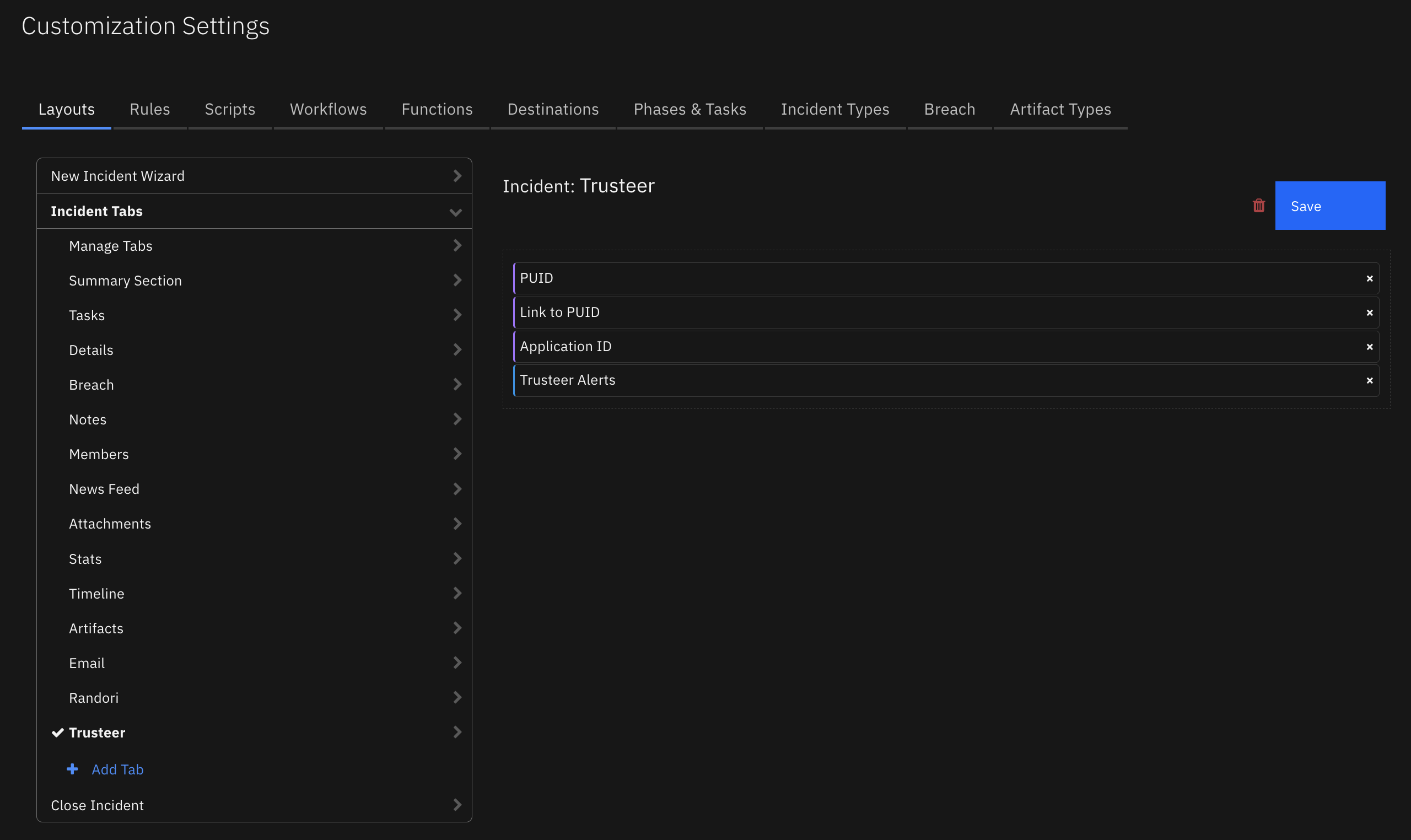
Data Table - Siemplify List Entries¶
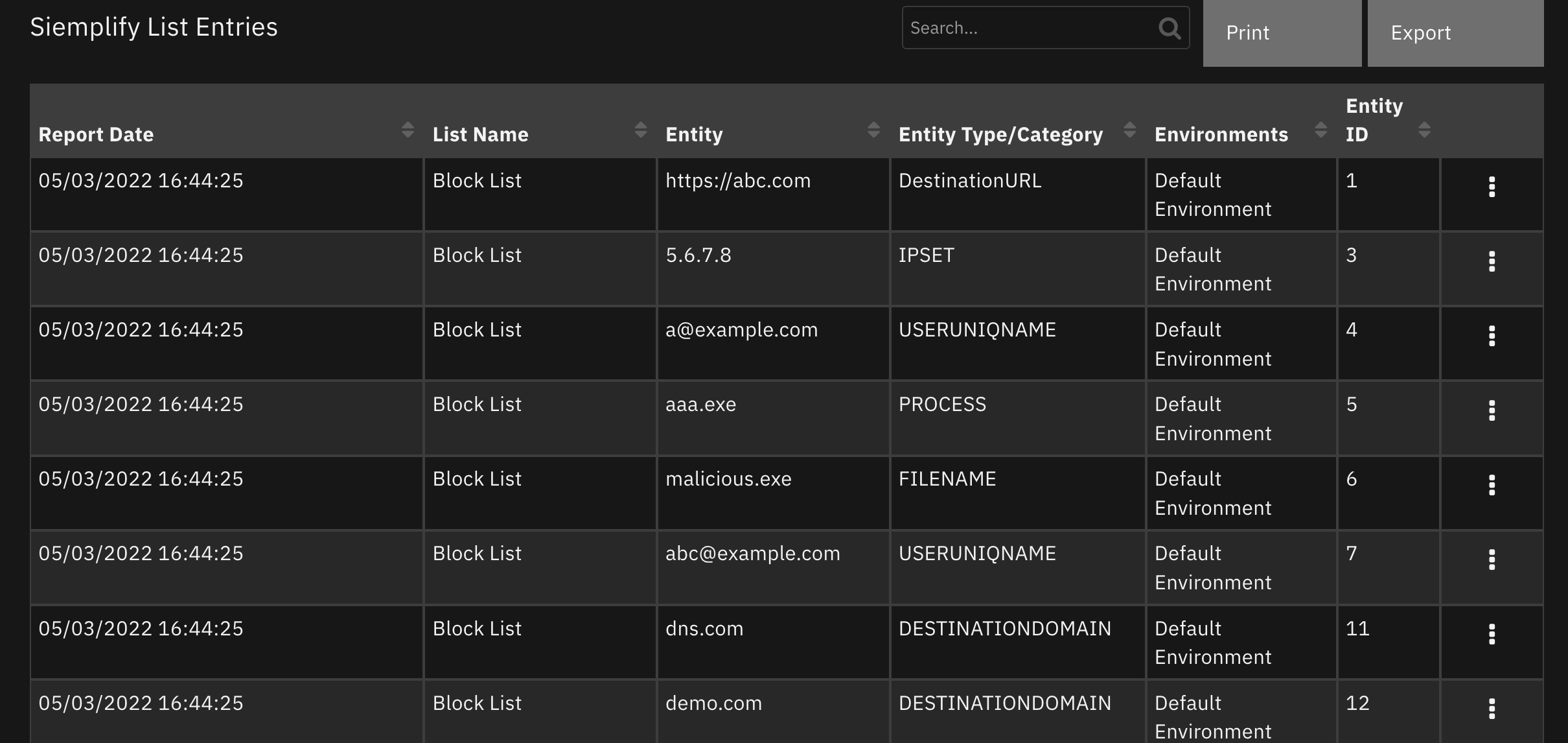
API Name:¶
siemplify_list_entries
Columns:¶
Column Name |
API Access Name |
Type |
Tooltip |
|---|---|---|---|
Entity |
|
|
- |
Entity ID |
|
|
- |
Entity Type/Category |
|
|
- |
Environments |
|
|
- |
List Name |
|
|
- |
Report Date |
|
|
- |
Custom Fields¶
Label |
API Access Name |
Type |
Prefix |
Placeholder |
Tooltip |
|---|---|---|---|---|---|
Siemplify Alert Id |
|
|
|
- |
Siemplify alert id used for synchronization |
Siemplify Assignee |
|
|
|
- |
Siemplify case assignee |
Siemplify Case Id |
|
|
|
- |
Siemplify case id used for synchronization |
Siemplify Case Link |
|
|
|
- |
URL link back to Case |
Siemplify Environment |
|
|
|
- |
- |
Siemplify Is Important |
|
|
|
- |
Siemplify IsImportant |
Siemplify Priority |
|
|
|
- |
Siemplify case priority |
Siemplify Stage |
|
|
|
- |
Siemplify case stage |
Siemplify Tags |
|
|
|
- |
comma separated list of tags used with this Case |
Rules¶
Rule Name |
Object |
Workflow Triggered |
Condition |
|---|---|---|---|
Siemplify Add Playbook |
incident |
|
|
Siemplify Auto Close Case |
incident |
|
|
Siemplify Auto Sync Artifact |
artifact |
|
|
Siemplify Auto Sync Attachment |
attachment |
|
|
Siemplify Auto Sync Case |
incident |
|
|
Siemplify Auto Sync Comment |
note |
|
|
Siemplify Remove Blocklist/Custom List Entity |
siemplify_list_entries |
|
|
Siemplify Sync Artifact |
artifact |
|
|
Siemplify Sync Case |
incident |
|
|
Siemplify Sync Comment |
note |
|
|
Siemplify Sync Task |
task |
|
|
Siemplify: Add/Update Entity to Blocklist |
artifact |
|
|
Siemplify: Add/Update Entity to Custom List |
artifact |
|
|
Siemplify: Get Blocklist Entities |
incident |
|
|
Siemplify: Get Custom List Entities |
incident |
|
|
Troubleshooting & Support¶
Refer to the documentation listed in the Requirements section for troubleshooting information.
For Support¶
This is a IBM Community provided app. Please search the Community ibm.biz/soarcommunity for assistance.