Guardium Insights Integration¶
Table of Contents¶
Release Notes¶
Version |
Date |
Notes |
|---|---|---|
1.0.1 |
01/2026 |
Added support for Python 3.12 |
1.0.0 |
08/2021 |
Initial Release |
Overview¶
Resilient Circuits Components for ‘fn_guardium_insights_integration’
This Resilient component support Guardum Insights version >= 3.0.
Resilient Circuits Components for ‘fn_guardium_insights_integration’
Key Features¶
Automatic Resilient incident’s creation based on realtime anomalies generated in Guardium Insights.
Block a specifiec user from Resilient
Generate classification report
Automatically populate the breach data types based on classification report data.
Automatically create artifacts based on anomalies data in each created incident.
Enrich who, what, when, where information for each created incidents.
Requirements¶
This app supports the IBM Resilient SOAR Platform and the IBM Cloud Pak for Security.
Resilient platform¶
The Resilient platform supports two app deployment mechanisms, App Host and integration server.
If deploying to a Resilient platform with an App Host, the requirements are:
Resilient platform >
51.0.0.The app is in a container-based format (available from the AppExchange as a
zipfile).
If deploying to a Resilient platform with an integration server, the requirements are:
Resilient platform >
51.0.0.The app is in the older integration format (available from the AppExchange as a
zipfile which contains atar.gzfile).Integration server is running
resilient_circuits>=51.0.0.If using an API key account, make sure the account provides the following minimum permissions:
Name |
Permissions |
|---|---|
Org Data |
Read |
Function |
Read |
Incident |
Create, Read, Edit Member |
Incident fields, Artifacts, Attachments, Milestones, Datatables |
Edit |
Notes |
Edit |
The following Resilient platform guides provide additional information:
App Host Deployment Guide:provides installation, configuration, and troubleshooting information, including proxy server settings.
Integration Server Guide: provides installation, configuration, and troubleshooting information, including proxy server settings.
System Administrator Guide: provides the procedure to install, configure and deploy apps.
The above guides are available on the IBM Knowledge Center at ibm.biz/resilient-docs. On this web page, select your Resilient platform version. On the follow-on page, you can find the App Host Deployment Guide or Integration Server Guide by expanding Resilient Apps in the Table of Contents pane. The System Administrator Guide is available by expanding System Administrator.
Cloud Pak for Security¶
If you are deploying to IBM Cloud Pak for Security, the requirements are:
IBM Cloud Pak for Security >= 1.10
Cloud Pak is configured with an App Host.
The app is in a container-based format (available from the AppExchange as a
zipfile).
The following Cloud Pak guides provide additional information:
App Host Deployment Guide: provides installation, configuration, and troubleshooting information, including proxy server settings. From the Table of Contents, select Case Management and Orchestration & Automation > Orchestration and Automation Apps.
System Administrator Guide: provides information to install, configure, and deploy apps. From the IBM Cloud Pak for Security Knowledge Center table of contents, select Case Management and Orchestration & Automation > System administrator.
These guides are available on the IBM Knowledge Center at ibm.biz/cp4s-docs. From this web page, select your IBM Cloud Pak for Security version. From the version-specific Knowledge Center page, select Case Management and Orchestration & Automation.
Proxy Server¶
The app does support a proxy server. proxy server configuration should done via app.configuration file.
Python Environment¶
Both Python 3.11 and Python 3.12 are supported. Additional package dependencies may exist for each of these packages:
resilient_circuits>=51.0.0
resilient_lib>=51.0.0’
resilient>=51.0.0
circuits>=3.2
six>=1.15.0
requests>=2.25.0
pytz>=2020.5
Installation¶
App Host¶
All the components for running this integration in a container already exist when using the App Host app.
To install,
Navigate to Administrative Settings and then the Apps tab.
Click the Install button and select the downloaded file: app-fn_guardium_insights_integration-x.x.x.zip.
Go to the Configuration tab and edit the app.config file, editing the url, access credentials, etc.
Config |
Required |
Example |
Description |
|---|---|---|---|
datatable_id |
Yes |
|
*Resilient data table to hold classification |
report data* |
|||
insights_host |
Yes |
`` |
Guardium Insights IP/DNS |
rest_service_port |
Yes |
|
Guardium Insights Restful Service port, By Default 8443 |
insights_encoded_token |
Yes |
`` |
Guardium Insights Restful service API Key Configuration. |
analytics_poll_time |
Yes |
`` |
*Periodic time interval to fetch anomalies from GI, poll time should be |
configured in seconds.* |
|||
report_period |
yes |
|
*classification report period, to populate breach data types data. |
values can be |
|||
report_fetch_size |
yes |
500 |
Maximum classification report records size. |
incident_member |
Yes |
`` |
Incident member to be added, for new created anomaly incidents. value can be group name, individual user account. If multiple value specified each should be separated by comma ex: user@domain.com, group_name. |
proxy |
Yes |
`` |
Guardium http/https proxy server address, leave blank for no proxy. |
insights_ca_file |
Yes |
|
Mention certificate path for SSL/TSL. Default Disabled. |
enable_firewall_auth |
Yes |
|
false - disable firewall authentication, true - enable firewall authentication. |
bso_ip |
Yes |
`` |
Firewall Server IP Address. |
bso_user |
Yes |
`` |
Firewall Auth User Name, should be given if |
bso_password |
Yes |
`` |
irewall Auth Password, should be given if |
Integration Server¶
Download the
app-fn_guardium_insights_integration-x.x.x.zip.Copy the
.zipto your Integration Server and SSH into it.Unzip the package:
$ unzip app-fn_guardium_insights_integration-x.x.x.zip
Install the package:
$ pip install fn_guardium_insights_integration-x.x.x.tar.gz
Import the configurations into your app.config file:
$ resilient-circuits config -u
Import the fn_guardium_insights_integration customizations into the Resilient platform:
$ resilient-circuits customize -y -l fn-guardium-insights-integration
Open the config file, scroll to the bottom and edit your fn_ansible_tower configurations:
$ nano ~/.resilient/app.config
App Configuration¶
Config |
Required |
Example |
Description |
|---|---|---|---|
datatable_id |
Yes |
|
*Resilient data table to hold classification |
report data* |
|||
insights_host |
Yes |
`` |
Guardium Insights IP/DNS |
rest_service_port |
Yes |
|
Guardium Insights Restful Service port, By Default 8443 |
insights_encoded_token |
Yes |
`` |
Guardium Insights Restful service API Key Configuration. |
analytics_poll_time |
Yes |
`` |
*Periodic time interval to fetch anomalies from GI, poll time should be |
configured in seconds.* |
|||
report_period |
yes |
|
classification report period, to populate breach data types data. values can be |
report_fetch_size |
yes |
500 |
Maximum classification report records size. |
incident_member |
Yes |
`` |
Incident member to be added, for new created anomaly incidents. value can be group name, individual user account. If multiple value specified each should be separated by comma ex: user@domain.com, group_name. |
proxy |
Yes |
`` |
Guardium http/https proxy server address, leave blank for no proxy. |
insights_ca_file |
Yes |
|
Mention certificate path for SSL/TSL. Default Disabled. |
enable_firewall_auth |
Yes |
|
*false - disable firewall authentication, true - enable firewall |
authentication.* |
|||
bso_ip |
Yes |
`` |
Firewall Server IP Address. |
bso_user |
Yes |
`` |
Firewall Auth User Name, should be given if |
bso_password |
Yes |
`` |
irewall Auth Password, should be given if |
Save and Close the app.config file.
Run resilient-circuits or restart the Service on Windows/Linux:
$ resilient-circuits run
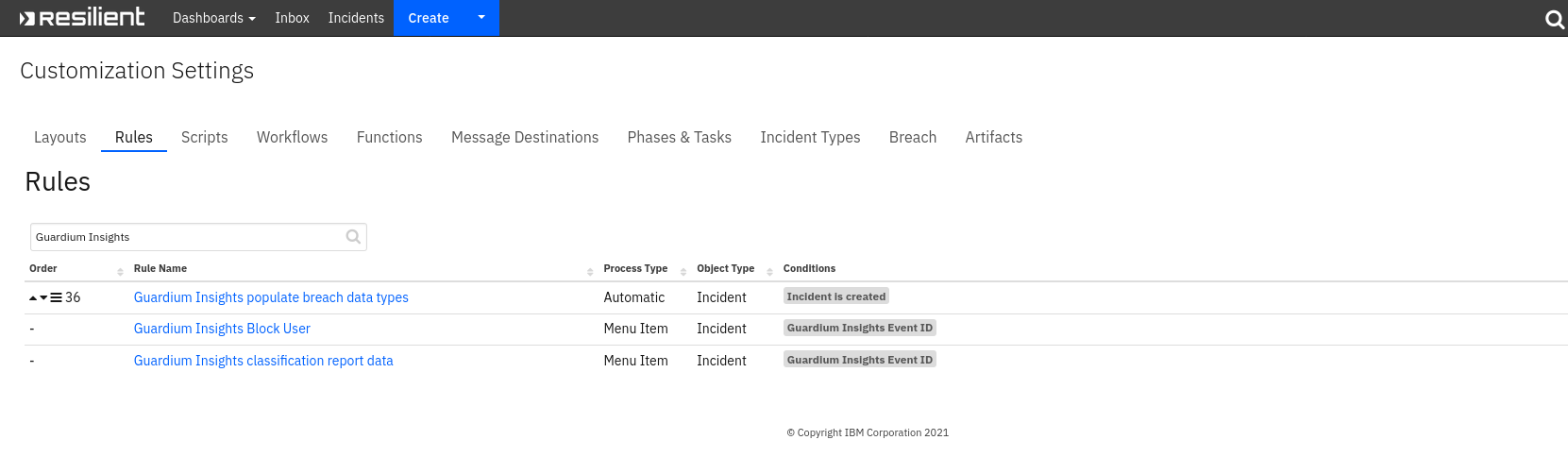
Custom Layouts¶
Import the Data Tables and Custom Fields like the screenshot below:
Function - Function Guardium Insights Block User¶
A Function to Block User From Guardium Insights.
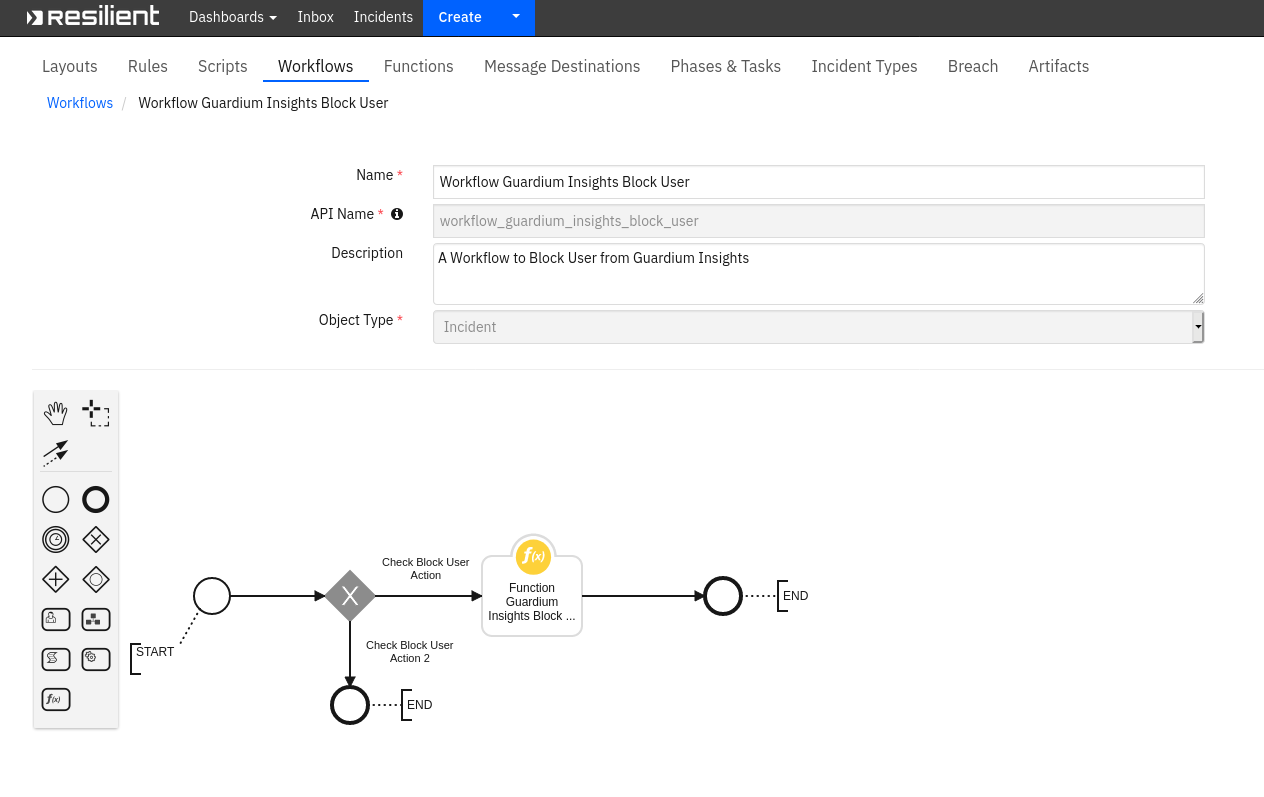
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
YES |
|
- |
|
|
YES |
|
- |
|
|
YES |
|
- |
|
|
YES |
|
- |
Outputs:
results = {
"version": "1.0",
"success": True,
"reason": None,
"content": {
"block_result": True,
"err": "no error"
},
"raw": "{\"block_result\": true, \"err\": \"no error\"}",
"inputs": {
"guardium_id": "grd_id",
"config_id": "0",
"database_user/actor/who": "DB_USER",
"what": {
"database_name": "SAMPLE",
"server_port": "PORT",
"service_name": "SERVICE_NAME",
"sever_hostname": "HOST_NAME",
"server_ip": "SERVER_IP"
}
},
"metrics": {
"version": "1.0",
"package": "fn-guardium-insights-integration",
"package_version": "1.0.0",
"host": "host_dns",
"execution_time_ms": 2671,
"timestamp": "2021-09-30 20:04:23"
}
}
Example Pre-Process Script:
inputs.input_field_guardium_insights_config_id = incident.properties.field_guardium_insights_config_id
inputs.input_field_guardium_insights_guardium_id = incident.properties.field_guardium_insights_global_id
inputs.input_field_guardium_insights_who = incident.properties.field_guardium_insights_who
inputs.input_field_guardium_insights_what = incident.properties.field_guardium_insights_what
Example Post-Process Script:
import re
notes_string = u"Block user action successful\n"
content = results.get("value", {}).get("content", {})
for k, v in content.items():
notes_string += u"{}: {}\n".format(k, str(v))
inputs_data = results.get("value", {}).get("inputs", {})
for k, v in inputs_data.items():
if k == "what":
for sub_k, sub_v in v.items():
notes_string += u"{}: {}\n".format(re.sub("_", " ", sub_k).title(), sub_v)
else:
notes_string += u"{}: {}\n".format(re.sub("_", " ", k).title(), v)
incident.addNote(notes_string)
Function - Function Guardium Insights Classification Report¶
A function to get classification report data.
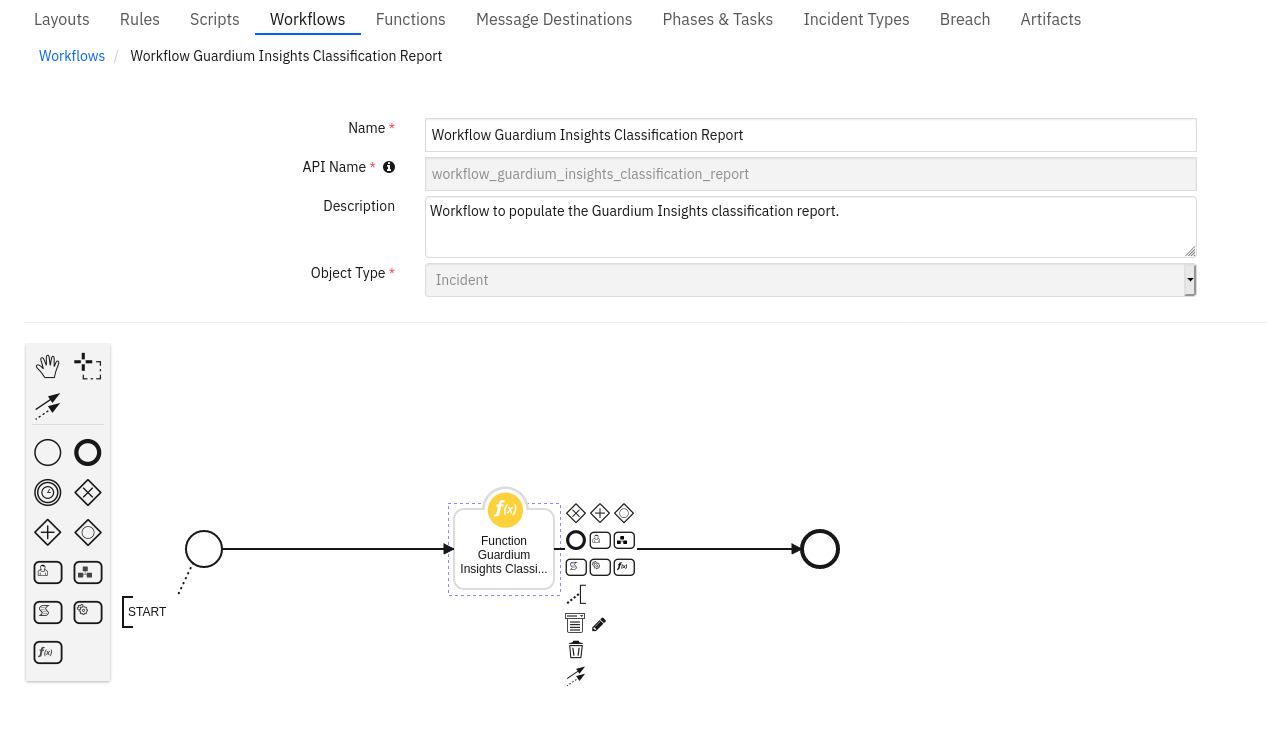
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
- |
|
|
Yes |
|
- |
|
|
Yes |
|
- |
|
|
Yes |
|
- |
|
|
No |
|
- |
|
|
No |
|
- |
Outputs:
results = {
"version": "1.0",
"success": True,
"reason": "Classification report generated successfully...",
"content": {},
"raw": "{}",
"inputs": {
"incident_id": 3805,
"input_field_guardium_insights_to_date": 1632940200000,
"input_field_guardium_insights_who": "Finance_GOE",
"input_field_guardium_insights_fetch_size": 5,
"input_field_guardium_insights_from_date": 1630434600000,
"input_field_guardium_insights_what": "{\"database_name\": \"database_name\", \"server_port\": \"server_port\", \"service_name\": \"service_name\", \"sever_hostname\": \"sever_hostname\", \"server_ip\": \"server_ip\"}"
},
"metrics": {
"version": "1.0",
"package": "fn-guardium-insights-integration",
"package_version": "1.0.0",
"host": "host",
"execution_time_ms": 11151,
"timestamp": "2021-09-30 20:26:48"
}
}
Example Pre-Process Script:
inputs.incident_id = incident.id
inputs.input_field_guardium_insights_who = incident.properties.field_guardium_insights_who
inputs.input_field_guardium_insights_what = incident.properties.field_guardium_insights_what
inputs.input_field_guardium_insights_from_date = rule.properties.act_field_guardium_insights_from_date
inputs.input_field_guardium_insights_to_date = rule.properties.act_field_guardium_insights_to_date
inputs.input_field_guardium_insights_fetch_size = rule.properties.act_field_guardium_insights_fetch_size
Example Post-Process Script:
report_st = results.get("value").get("reason")
incident.addNote(report_st)
Function - Function Guardium Insights populate breach data types¶
A function to populate the incident breach data types.
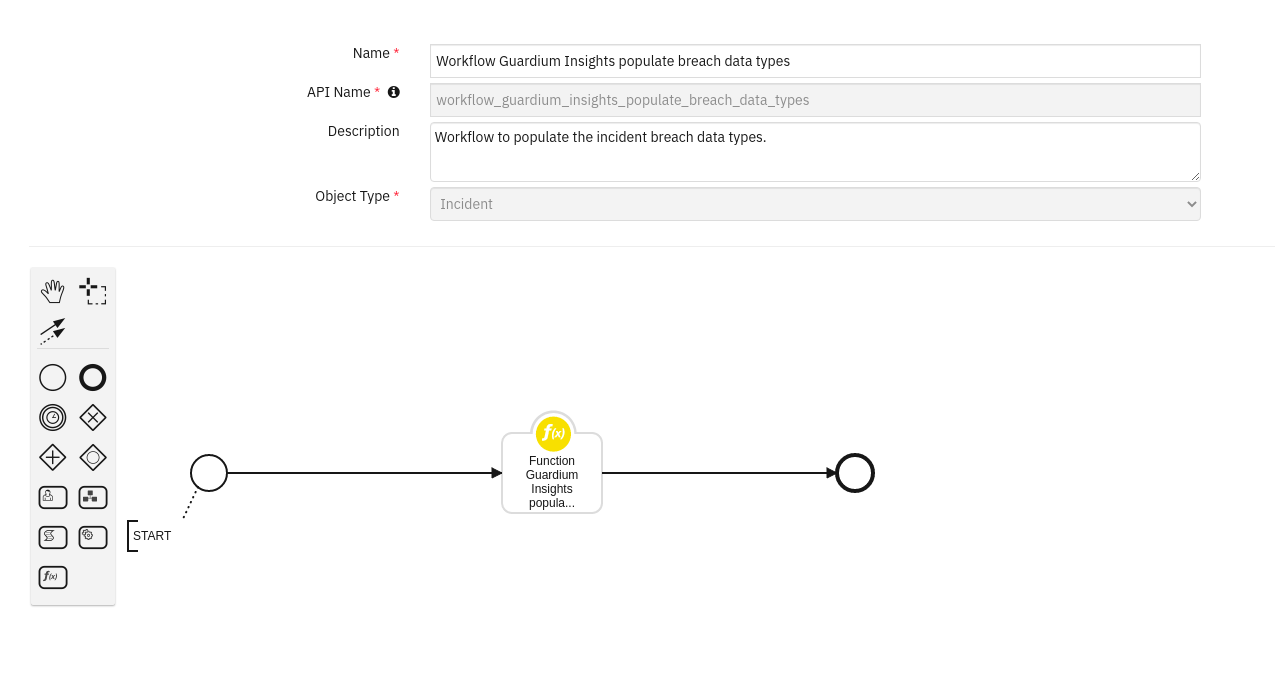
Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
- |
|
|
No |
|
- |
|
|
No |
|
- |
Outputs:
results = {
"version": "1.0",
"success": False,
"reason": "populating breach data types completed: incident ID3810",
"content": {},
"raw": "{}",
"inputs": {
"incident_id": 3810,
"input_field_guardium_insights_who": "Finance_GOE",
"input_field_guardium_insights_what": "{\"database_name\": \"database_name\", \"server_port\": \"server_port\", \"service_name\": \"service_name\", \"sever_hostname\": \"sever_hostname\", \"server_ip\": \"server_ip\"}"
},
"metrics": {
"version": "1.0",
"package": "fn-guardium-insights-integration",
"package_version": "1.0.0",
"host": "host",
"execution_time_ms": 6250,
"timestamp": "2021-09-30 20:36:00"
}
}
Example Pre-Process Script:
inputs.incident_id = incident.id
inputs.input_field_guardium_insights_who = incident.properties.field_guardium_insights_who
inputs.input_field_guardium_insights_what = incident.properties.field_guardium_insights_what
Example Post-Process Script:
None
Data Table - Guardium Insights Classification Report¶
API Name:¶
guardium_insights_classification_report
Columns:¶
Column Name |
API Access Name |
Type |
Tooltip |
|---|---|---|---|
Catalog |
|
|
- |
Category |
|
|
- |
Classification name |
|
|
- |
Classification rule |
|
|
- |
Column |
|
|
- |
Comprehensive |
|
|
- |
Datasource IP |
|
|
- |
Datasource name |
|
|
- |
Datasource type |
|
|
- |
Date Created |
|
|
- |
Description |
|
|
- |
Port |
|
|
- |
Schema |
|
|
- |
Service name |
|
|
- |
Start Date(local time) |
|
|
- |
Table |
|
|
- |
Custom Fields¶
Label |
API Access Name |
Type |
Prefix |
Placeholder |
Tooltip |
|---|---|---|---|---|---|
what |
|
|
|
- |
- |
when |
|
|
|
- |
- |
Guardium Insights Config ID |
|
|
|
- |
- |
where |
|
|
|
- |
- |
Guardium Insights Event ID |
|
|
|
- |
- |
who |
|
|
|
- |
- |
Guardium Insights Global ID |
|
|
|
- |
- |
why |
|
|
|
- |
- |
Rules¶
Rule Name |
Object |
Workflow Triggered |
|---|---|---|
Guardium Insights Block User |
incident |
|
Guardium Insights classification report data |
incident |
|
Troubleshooting & Support¶
Refer to the documentation listed in the Requirements section for troubleshooting information.
For Support¶
This is a IBM Community provided App. Please search the Community https://ibm.biz/resilientcommunity for assistance.