QRadar EDR¶
Table of Contents¶
History¶
Version |
Date |
Notes |
|---|---|---|
1.0.0 |
03/2022 |
Initial Release |
1.1.0 |
08/2023 |
Convert Rules and Workflows to Playbooks |
1.2.0 |
09/2023 |
Added support to deisolate a previously isolated endpoint and renamed application to QRadar EDR |
1.3.0 |
10/2023 |
Rename Reaqta Functions and Playbooks to QRadar EDR |
Release Notes¶
1.3.0¶
In v1.3.0, since Reaqta has been renamed to QRadar EDR, all the labels of functions and playbooks are renamed to refect the product name change.
1.2.0 ¶
In v1.2.0, the applications name has been updated to QRadar EDR and the existing rules and workflows have been replaced with playbooks. This change is made to support the ongoing, newer capabilities of playbooks. Each playbook has the same functionality as the previous, corresponding rule/workflow.
If upgrading from a previous release, you’ll notice that the previous release’s rules/workflows remain in place. Both sets of rules and playbooks are active. For manual actions, playbooks have the same name as it’s corresponding rule, but with “(PB)” added at the end.
You can continue to use the rules/workflows. But migrating to playbooks provides greater functionality along with future app enhancements and bug fixes.¶
Overview¶
IBM SOAR app bidirectional synchronization and functions for QRadar EDR
Bidirectional synchronization of QRadar EDR (formally known as ReaQta) Alerts to IBM SOAR.
Additional functions exists to list and kill endpoint processes, isolate the endpoint and synchronize notes and close events.
Key Features¶
Sync alerts to SOAR cases via user defined filter criteria
Sync SOAR case notes to QRadar EDR
QRadar EDR alert closing closes the SOAR case and SOAR case closing closes the QRadar EDR alert
Get running processes on a give endpoint
Download QRadar EDR endpoint process file to an attachment
Kill QRadar EDR endpoint processes
Isolate QRadar EDR endpoint
Create a new Alert or Blocking policy based on a file hash
Requirements¶
This app supports the IBM Security QRadar SOAR Platform and the IBM Security QRadar SOAR for IBM Cloud Pak for Security.
SOAR platform¶
The SOAR platform supports two app deployment mechanisms, Edge Gateway (formerly App Host) and integration server.
If deploying to a SOAR platform with an Edge Gateway, the requirements are:
SOAR platform >=
46.0.8131.The app is in a container-based format (available from the AppExchange as a
zipfile).
If deploying to a SOAR platform with an integration server, the requirements are:
SOAR platform >=
46.0.8131.The app is in the older integration format (available from the AppExchange as a
zipfile which contains atar.gzfile).Integration server is running
resilient-circuits>=46.0.0.If using an API key account, make sure the account provides the following minimum permissions:
Name
Permissions
Org Data
Read
Function
Read
The following SOAR platform guides provide additional information:
Edge Gateway Deployment Guide or App Host Deployment Guide: provides installation, configuration, and troubleshooting information, including proxy server settings.
Integration Server Guide: provides installation, configuration, and troubleshooting information, including proxy server settings.
System Administrator Guide: provides the procedure to install, configure and deploy apps.
The above guides are available on the IBM Documentation website at ibm.biz/soar-docs. On this web page, select your SOAR platform version. On the follow-on page, you can find the Edge Gateway Deployment Guide, App Host Deployment Guide, or Integration Server Guide by expanding Apps in the Table of Contents pane. The System Administrator Guide is available by expanding System Administrator.
Cloud Pak for Security¶
If you are deploying to IBM Cloud Pak for Security, the requirements are:
IBM Cloud Pak for Security >=
1.8.Cloud Pak is configured with an Edge Gateway.
The app is in a container-based format (available from the AppExchange as a
zipfile).
The following Cloud Pak guides provide additional information:
Edge Gateway Deployment Guide or App Host Deployment Guide: provides installation, configuration, and troubleshooting information, including proxy server settings. From the Table of Contents, select Case Management and Orchestration & Automation > Orchestration and Automation Apps.
System Administrator Guide: provides information to install, configure, and deploy apps. From the IBM Cloud Pak for Security IBM Documentation table of contents, select Case Management and Orchestration & Automation > System administrator.
These guides are available on the IBM Documentation website at ibm.biz/cp4s-docs. From this web page, select your IBM Cloud Pak for Security version. From the version-specific IBM Documentation page, select Case Management and Orchestration & Automation.
Proxy Server¶
The app does support a proxy server.
Python Environment¶
Python 3.6 and Python 3.9 are supported. Additional package dependencies may exist for each of these packages:
cachetools
resilient-circuits>=46.0.0
retry2
Development Version¶
This app has been implemented using:
Product Name |
Product Version |
API URL |
API Version |
|---|---|---|---|
ReaQta Hive |
3.7 |
rqt-api/1/ |
1 |
Configuration¶
In order to make API calls to QRadar EDR, create an API Application, providing the endpoint group restrictions as appropriate. The API ID and secret will be copied into your app.config file
Installation¶
Install¶
To install or uninstall an App or Integration on the SOAR platform, see the documentation at ibm.biz/soar-docs.
To install or uninstall an App on IBM Cloud Pak for Security, see the documentation at ibm.biz/cp4s-docs and follow the instructions above to navigate to Orchestration and Automation.
App Configuration¶
The following table provides the settings you need to configure the app. These settings are made in the app.config file. See the documentation discussed in the Requirements section for the procedure.
[fn_reaqta] ¶
This section defines the global settings, including the poller configuration. For each hive, use the section definition below
Config |
Required |
Example |
Description |
|---|---|---|---|
polling_interval |
Yes |
|
*Number of seconds between polling queries for new alerts * |
polling_lookback |
Yes |
|
Number of minutes to look back for new alerts the first time the app starts or restarts |
soar_create_case_template |
No |
|
Override template used to create a SOAR case from the poller. See Templates for SOAR Cases |
soar_close_case_template |
No |
|
Override template used to close a SOAR case from the poller. See Templates for SOAR Cases |
https_proxy |
No |
|
Proxy URL for HTTPS connections |
http_proxy |
No |
|
Proxy URL for HTTP connections |
timeout |
No |
|
Seconds to wait for APIs calls back to QRadar EDR. Default is 30 |
polling_hives |
Yes |
hive_label1, hive_label2 |
Comma separated list of hives to poll. |
policy_hives |
Yes |
hive_label1, hive_label2 |
Comma separated list of hives to set a policy if not specified from the SOAR function call |
[fn_reaqta:hive_label] ¶
Repeat this section for each ReaQta hive. Add the hive_label used in the polling_hives parameter above.
Config |
Required |
Example |
Description |
|---|---|---|---|
reaqta_url |
Yes |
|
Base URL to ReaQta instance ending in slash ‘/’ |
api_key |
Yes |
|
API Key ID from your configured ReaQta API application |
api_secret |
Yes |
|
API Key secret from your configured ReaQta API application |
api_version |
Yes |
|
API version portion of url to append to reaqta_url, ending in slash ‘/’ |
cafile |
Yes |
|
Path to your ReaQta client certificate, if needed or false for no certificate verification |
polling_filters |
No |
“severity”: [“medium”, “high”], “tag”: [“hive”], “groups”: [“groupA”, “groupB”], “impact”: 70 |
Set filters for the poller. Groups are either Client or Group names. Impact compares alerts greater or equal to this value |
Custom Layouts¶
Import the Data Tables and Custom Fields like the screenshot below:
Poller Considerations¶
The poller is just one way to escalate ReaQta alerts to SOAR cases. It’s also possible to send alert information to a SIEM, such as IBM QRadar, which would then corelate alerts into Offenses. With the QRadar Plugin for SOAR, offenses can then be escalated to SOAR cases. As long as the ReaQta alert ID is preserved in the custom case field reaqta_id and reaqta_hive, then all the remaining details about the alert will synchronize to the SOAR case. In the case of the QRadar Plugin for SOAR, you would modify the escalation templates to reference this custom field with the ReaQta Alert ID.
When using another source of ReaQta Alert escalation to IBM SOAR, disable the poller by changing the app.config setting to poller_interval=0.
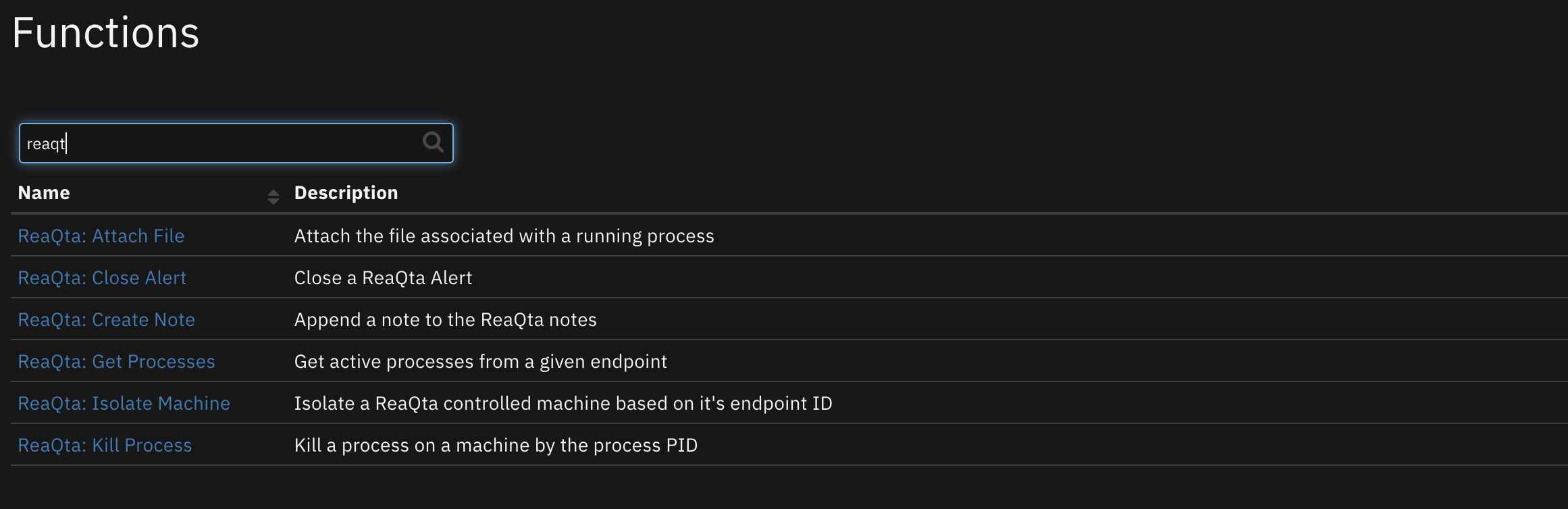
Function - QRadar EDR: Attach File¶
Attach the file associated with a running process

Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
- |
|
|
No |
|
Label used to identify which ReaQta hive this alert is associated with |
|
|
Yes |
|
- |
|
|
Yes |
|
- |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"actions": [],
"content_type": "application/x-msdownload",
"created": 1691389665926,
"creator_id": 9,
"id": 32,
"inc_id": 2154,
"inc_name": "ReaQta Alert - Detection Strategy, Endpoint: ACTIVEDIRECTORY",
"inc_owner": 8,
"name": "powershell.exe",
"playbooks": [],
"reconciliation_status": "matched",
"size": 720768,
"task_at_id": null,
"task_custom": null,
"task_id": null,
"task_members": null,
"task_name": null,
"type": "incident",
"uuid": "b50616ee-8c1b-4830-a0d5-601b3a550ab9",
"vers": 8
},
"inputs": {
"reaqta_endpoint_id": "836686917654282240",
"reaqta_hive": "rhiveam",
"reaqta_incident_id": 2154,
"reaqta_program_path": "c:\\windows\\system32\\windowspowershell\\v1.0\\powershell.exe"
},
"metrics": {
"execution_time_ms": 22507,
"host": "local",
"package": "fn-reaqta",
"package_version": "1.1.0",
"timestamp": "2023-08-07 14:27:46",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.reaqta_program_path = row['program_path']
inputs.reaqta_endpoint_id = incident.properties.reaqta_endpoint_id
inputs.reaqta_incident_id = incident.id
inputs.reaqta_hive = incident.properties.reaqta_hive
Example Function Post Process Script:
results = playbook.functions.results.create_attach_results
if results.success:
incident.addNote(u"ReaQta Attach File created: {} from program path: {}".format(results.content['name'], results.inputs['reaqta_program_path']))
else:
incident.addNote(u"ReaQta Attach File failed: {}".format(results.reason))
Function - QRadar EDR: Close Alert¶
Close a ReaQta Alert

Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
- |
|
|
No |
|
Label used to identify which ReaQta hive this alert is associated with |
|
|
Yes |
|
- |
|
|
No |
|
- |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"alertId": "1024257396198866946",
"closed": true
},
"inputs": {
"reaqta_alert_id": "1024257396198866946",
"reaqta_hive": "rhiveam",
"reaqta_is_malicious": false,
"reaqta_note": "\u003cdiv class=\"rte\"\u003e\u003cdiv\u003eclosing\u003c/div\u003e\u003c/div\u003e"
},
"metrics": {
"execution_time_ms": 932,
"host": "local",
"package": "fn-reaqta",
"package_version": "1.1.0",
"timestamp": "2023-08-07 14:34:06",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
# Modify this table for custom resolution types
IS_MALICIOUS_LOOKUP = {
7: False, # Unresolved
8: False, # Duplicate
9: False, # Not a Issue
10: True # Resolved
}
inputs.reaqta_alert_id = incident.properties.reaqta_id
inputs.reaqta_note = incident.resolution_summary.content
inputs.reaqta_is_malicious = IS_MALICIOUS_LOOKUP.get(incident.resolution_id, False) # if resolution_id is not found, set to not malicious
inputs.reaqta_hive = incident.properties.reaqta_hive
Example Function Post Process Script:
None
Function - QRadar EDR: Create Artifact¶
Create an artifact from a ReaQta endpoint process file

Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
- |
|
|
Yes |
|
- |
|
|
No |
|
Label used to identify which ReaQta hive this alert is associated with |
|
|
Yes |
|
- |
|
|
Yes |
|
- |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": [
{
"actions": [],
"attachment": {
"actions": [],
"content_type": "application/x-msdownload",
"created": 1691389806738,
"creator_id": 9,
"id": 33,
"inc_id": 2154,
"inc_name": "ReaQta Alert - Detection Strategy, Endpoint: ACTIVEDIRECTORY",
"inc_owner": 8,
"name": "smss.exe",
"playbooks": [],
"reconciliation_status": "matched",
"size": 214866,
"task_at_id": null,
"task_custom": null,
"task_id": null,
"task_members": null,
"task_name": null,
"type": "artifact",
"uuid": "275ab471-16b0-4c1e-aed0-15c2ad940931",
"vers": 9
},
"created": 1691389806319,
"creator_principal": {
"display_name": "dev-integration",
"id": 9,
"name": "c3be9c35-c18c-4fac-bae5-9a7d483f1db2",
"type": "apikey"
},
"description": "Extracted from ReaQta",
"global_artifact": [],
"global_info": null,
"hash": "dc968f62938179dc007bced955b9a27c1a9949e00f168868c5e68fbff5742f93",
"hits": [],
"id": 313,
"inc_id": 2154,
"inc_name": "ReaQta Alert - Detection Strategy, Endpoint: ACTIVEDIRECTORY",
"inc_owner": 8,
"ip": {
"destination": null,
"source": null
},
"last_modified_by": {
"display_name": "dev-integration",
"id": 9,
"name": "c3be9c35-c18c-4fac-bae5-9a7d483f1db2",
"type": "apikey"
},
"last_modified_time": 1691389806757,
"parent_id": null,
"pending_scan_result": false,
"pending_sources": [],
"perms": null,
"playbooks": [],
"properties": null,
"related_incident_count": null,
"relating": true,
"type": 12,
"value": "smss.exe"
},
{
"actions": [],
"attachment": null,
"created": 1691389806467,
"creator_principal": {
"display_name": "dev-integration",
"id": 9,
"name": "c3be9c35-c18c-4fac-bae5-9a7d483f1db2",
"type": "apikey"
},
"description": "Extracted from ReaQta",
"global_artifact": [],
"global_info": null,
"hash": "31ab03c62b67b4d4162d9c5d92212cd732cc664ec65926c938c71c30d731f53f",
"hits": [],
"id": 314,
"inc_id": 2154,
"inc_name": "ReaQta Alert - Detection Strategy, Endpoint: ACTIVEDIRECTORY",
"inc_owner": 8,
"ip": {
"destination": null,
"source": null
},
"last_modified_by": {
"display_name": "dev-integration",
"id": 9,
"name": "c3be9c35-c18c-4fac-bae5-9a7d483f1db2",
"type": "apikey"
},
"last_modified_time": 1691389806476,
"parent_id": 313,
"pending_scan_result": false,
"pending_sources": [],
"perms": null,
"playbooks": [],
"properties": null,
"related_incident_count": null,
"relating": true,
"type": 13,
"value": "c5e36a0098f54a6d4bf33037c5c68bf4"
},
{
"actions": [],
"attachment": null,
"created": 1691389806491,
"creator_principal": {
"display_name": "dev-integration",
"id": 9,
"name": "c3be9c35-c18c-4fac-bae5-9a7d483f1db2",
"type": "apikey"
},
"description": "Extracted from ReaQta",
"global_artifact": [],
"global_info": null,
"hash": "b41a290abff3ef1770ec7570fcee8575e7bb93a995c562119709087fdbd933ea",
"hits": [],
"id": 315,
"inc_id": 2154,
"inc_name": "ReaQta Alert - Detection Strategy, Endpoint: ACTIVEDIRECTORY",
"inc_owner": 8,
"ip": {
"destination": null,
"source": null
},
"last_modified_by": {
"display_name": "dev-integration",
"id": 9,
"name": "c3be9c35-c18c-4fac-bae5-9a7d483f1db2",
"type": "apikey"
},
"last_modified_time": 1691389806500,
"parent_id": 313,
"pending_scan_result": false,
"pending_sources": [],
"perms": null,
"playbooks": [],
"properties": null,
"related_incident_count": null,
"relating": true,
"type": 14,
"value": "cc7cdc7674ebaa353386f4529c800cd78ac5dd88"
},
{
"actions": [],
"attachment": null,
"created": 1691389806514,
"creator_principal": {
"display_name": "dev-integration",
"id": 9,
"name": "c3be9c35-c18c-4fac-bae5-9a7d483f1db2",
"type": "apikey"
},
"description": "Extracted from ReaQta",
"global_artifact": [],
"global_info": null,
"hash": "23596a1e546d7c2aaa48e72c615bb1d72690da5559454acda41c4eb7ab07b2cf",
"hits": [],
"id": 316,
"inc_id": 2154,
"inc_name": "ReaQta Alert - Detection Strategy, Endpoint: ACTIVEDIRECTORY",
"inc_owner": 8,
"ip": {
"destination": null,
"source": null
},
"last_modified_by": {
"display_name": "dev-integration",
"id": 9,
"name": "c3be9c35-c18c-4fac-bae5-9a7d483f1db2",
"type": "apikey"
},
"last_modified_time": 1691389806743,
"parent_id": 313,
"pending_scan_result": false,
"pending_sources": [],
"perms": null,
"playbooks": [],
"properties": null,
"related_incident_count": null,
"relating": true,
"type": 38,
"value": "5580c55feaeaeb35e8a9f88dd9dac69d70acaacfabb39012c7ae9c26b4c2a239"
}
],
"inputs": {
"reaqta_artifact_type": "Malware Sample",
"reaqta_endpoint_id": "836686917654282240",
"reaqta_hive": "rhiveam",
"reaqta_incident_id": 2154,
"reaqta_program_path": "C:\\Windows\\System32\\smss.exe"
},
"metrics": {
"execution_time_ms": 21204,
"host": "local",
"package": "fn-reaqta",
"package_version": "1.1.0",
"timestamp": "2023-08-07 14:30:07",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.reaqta_incident_id = incident.id
inputs.reaqta_endpoint_id = incident.properties.reaqta_endpoint_id
inputs.reaqta_program_path = row['process_path']
inputs.reaqta_artifact_type = "Malware Sample"
inputs.reaqta_hive = incident.properties.reaqta_hive
Example Function Post Process Script:
results = playbook.functions.results.create_artifact_results
if not results.success:
incident.addNote("ReaQta Create Artifact failed: {}".format(results.reason))
else:
incident.addNote(u"ReaQta Artifact created: {}".format(results.inputs['reaqta_program_path']))
Function - QRadar EDR: Create Note¶
Append a note to the ReaQta notes

Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
- |
|
|
No |
|
Label used to identify which ReaQta hive this alert is associated with |
|
|
No |
|
- |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"note": "{\"notes\":\"An attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\nIBM SOAR 15/08/2023 15:19:23\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\n\\n[SOAR Case - 3490](https://9.30.229.231:443/#incidents/3490)\\nIBM SOAR 15/08/2023 15:19:43\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\nIBM SOAR 15/08/2023 15:19:23\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\n\\n[SOAR Case - 3490](https://9.30.229.231:443/#incidents/3490)\\n\\n[SOAR Case - 13804](https://uax01.americas.cloudpaksecurity.com:443/app/respond/#cases/13804)\\nIBM SOAR 15/08/2023 16:19:54\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\nIBM SOAR 15/08/2023 15:19:23\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\n\\n[SOAR Case - 3490](https://9.30.229.231:443/#incidents/3490)\\n\\n[SOAR Case - 2097](https://calluses1.fyre.ibm.com:443/#incidents/2097)\\nIBM SOAR 15/08/2023 15:20:07\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\nIBM SOAR 15/08/2023 15:19:23\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\n\\n[SOAR Case - 3490](https://9.30.229.231:443/#incidents/3490)\\nIBM SOAR 15/08/2023 15:19:43\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\nIBM SOAR 15/08/2023 15:19:23\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\n\\n[SOAR Case - 3490](https://9.30.229.231:443/#incidents/3490)\\n\\n[SOAR Case - 13804](https://uax01.americas.cloudpaksecurity.com:443/app/respond/#cases/13804)\\n\\n[SOAR Case - 3492](https://9.30.229.231:443/#incidents/3492)\\nIBM SOAR 15/08/2023 15:14:47\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\nIBM SOAR 15/08/2023 15:19:23\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\n\\n[SOAR Case - 3490](https://9.30.229.231:443/#incidents/3490)\\nIBM SOAR 15/08/2023 15:19:43\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\nIBM SOAR 15/08/2023 15:19:23\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\n\\n[SOAR Case - 3490](https://9.30.229.231:443/#incidents/3490)\\n\\n[SOAR Case - 13804](https://uax01.americas.cloudpaksecurity.com:443/app/respond/#cases/13804)\\nIBM SOAR 15/08/2023 16:19:54\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\nIBM SOAR 15/08/2023 15:19:23\\nAn attempt to run encoded commands in the command line has been detected, often used to obfuscate malicious intent.\\n\\n[SOAR Case - 3490](https://9.30.229.231:443/#incidents/3490)\\n\\n[SOAR Case - 2097](https://calluses1.fyre.ibm.com:443/#incidents/2097)\\n\\n[SOAR Case - 3731](https://deployment-yfrujyoe.xdr.security.ibm.com:443/app/respond/#cases/3731)\\nIBM SOAR 16/08/2023 08:10:11\\nEndpoint Machine Isolated\\nIBM SOAR 16/08/2023 08:10:57\\nEndpoint Machine Deisolated\\nIBM SOAR 16/08/2023 08:13:17\\nEndpoint Machine Isolated\\nIBM SOAR 16/08/2023 08:14:30\\nEndpoint Machine Deisolated\"}"
},
"inputs": {
"reaqta_alert_id": "1029755084809961474",
"reaqta_hive": "rHiveam",
"reaqta_note": "Endpoint Machine Deisolated"
},
"metrics": {
"execution_time_ms": 600,
"host": "appHost",
"package": "fn-reaqta",
"package_version": "1.1.0",
"timestamp": "2023-08-16 08:14:31",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.reaqta_alert_id = incident.properties.reaqta_id
inputs.reaqta_note = note.text.content
inputs.reaqta_hive = incident.properties.reaqta_hive
Example Function Post Process Script:
from datetime import datetime
results = playbook.functions.results.reaqta_create_note_result
if results.success:
# Get the current time
dt_now = datetime.now()
note.text = u"<b>Sent to ReaQta at {0}</b><br>{1}".format(dt_now, str(note.text.content))
else:
incident.addNote("Sent Note to ReaQta failed: {}".format(results.reason))
Function - QRadar EDR: Create Policy¶
Create an alert trigger based on a program’s SHA256 hash

Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
No |
|
comma separated list of hives to create policies |
|
|
Yes |
|
Yes - Block hash, No - Create alert only |
|
|
No |
|
- |
|
|
Yes |
|
Enable/disable policy when created |
|
|
No |
|
Comma separated list of excluded groups for this policy |
|
|
No |
|
Comma separated list of included groups for this policy |
|
|
No |
|
- |
|
|
Yes |
|
Program file sh256 hash |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": [
{
"actions": [
2
],
"created": "2023-08-07T06:53:55.516Z",
"default": false,
"deleted": false,
"description": "",
"enabled": true,
"id": "1026728858289700868",
"lastModified": "2023-08-07T06:53:55.516Z",
"matchers": [
{
"alg": 1,
"hash": "de96a6e69944335375dc1ac238336066889d9ffc7d73628ef4fe1b1b160ab32c",
"id": "1026728858289709062",
"type": 2
}
],
"policy_hive": "rhiveam",
"policy_url": "https://rhiveam.techzone.ibm.com/policies/details/1026728858289700868",
"scope": "global",
"title": "test 123",
"type": 2,
"versionId": "1026728858289704965"
}
],
"inputs": {
"reaqta_hives": "rhiveam",
"reaqta_policy_block": false,
"reaqta_policy_description": "",
"reaqta_policy_enabled": true,
"reaqta_policy_excluded_groups": null,
"reaqta_policy_included_groups": null,
"reaqta_policy_title": "test 123",
"reaqta_sha256": "de96a6e69944335375dc1ac238336066889d9ffc7d73628ef4fe1b1b160ab32c"
},
"metrics": {
"execution_time_ms": 1317,
"host": "local",
"package": "fn-reaqta",
"package_version": "1.1.0",
"timestamp": "2023-08-07 14:53:55",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.reaqta_sha256 = row['sha256_hash']
inputs.reaqta_policy_title = playbook.inputs.reaqta_policy_title
inputs.reaqta_policy_description = playbook.inputs.reaqta_policy_description or ''
inputs.reaqta_policy_included_groups = playbook.inputs.reaqta_policy_included_groups
inputs.reaqta_policy_excluded_groups = playbook.inputs.reaqta_policy_excluded_groups
inputs.reaqta_policy_enabled = True
inputs.reaqta_policy_block = playbook.inputs.reaqta_policy_block_when_triggered
inputs.reaqta_hives = incident.properties.reaqta_hive
Example Function Post Process Script:
results = playbook.functions.results.reaqta_create_policy_result
if results.success:
policies = []
policies.append("<br>Policy Parameters:<br>Hives: {}<br>Title: {}<br>Description: {}<br>Included Groups: {}<br>Excluded Groups: {}<br>Enabled: {}<br>Block when Triggered: {}<br>".\
format(incident.properties.reaqta_hive,
playbook.inputs.reaqta_policy_title,
playbook.inputs.reaqta_policy_description,
playbook.inputs.reaqta_policy_included_groups,
playbook.inputs.reaqta_policy_excluded_groups,
None,
playbook.inputs.reaqta_policy_block_when_triggered))
for policy in results.content:
policies.append('Hive: {0} <a href="{1}" target="blank">{1}</a>'.format(policy.get('policy_hive'), policy.get("policy_url")))
incident.addNote(helper.createRichText("ReaQta Create Policies successful: {}".format("<br>".join(policies))))
else:
incident.addNote(helper.createRichText("ReaQta Create Policy failed: {}".format(results.reason)))
Function - QRadar EDR: Deisolate Machine¶
De-isolate a previously isolated ReaQta controlled machine based on it’s endpoint ID

Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
- |
|
|
No |
|
Label used to identify which ReaQta hive this alert is associated with |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"success": true
},
"inputs": {
"reaqta_endpoint_id": "836686917654282240",
"reaqta_hive": "rhive"
},
"metrics": {
"execution_time_ms": 783,
"host": "Apphost",
"package": "fn-reaqta",
"package_version": "1.1.0",
"timestamp": "2023-08-16 08:14:28",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.reaqta_endpoint_id = incident.properties.reaqta_endpoint_id
inputs.reaqta_hive = incident.properties.reaqta_hive
Example Function Post Process Script:
results = playbook.functions.results.reaqta_deisolate_machine_result
if results.success and results.content.get('success'):
msg = "Endpoint Machine Deisolated"
elif results.reason:
msg = u"ReaQta Deisolate Machine failed: {}".format(results.reason)
else:
msg = u"ReaQta Deisolate Machine failed: {}".format(results.content.get('message'))
incident.addNote(msg)
Function - QRadar EDR: Get Alert Information¶
Get all the ReaQta Alert information to populate custom fields and datatables

Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
- |
|
|
No |
|
Label used to identify which ReaQta hive this alert is associated with |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"activityState": "archived",
"alert_url": "https://rhiveam.techzone.ibm.com/alerts/1022070806768779266",
"byTypeEventCount": [
{
"count": 3,
"type": 2
},
{
"count": 1,
"type": 3
},
{
"count": 1,
"type": 28
},
{
"count": 1,
"type": 30
}
],
"closed": true,
"closedAt": "2023-07-27T00:00:01.673Z",
"endpoint": {
"agentVersion": "3.10.1",
"arch": 2,
"avInstalled": false,
"componentsVersions": [
{
"build": "27.1668701555901.commit",
"name": "keeper",
"version": "3.10.1"
},
{
"build": "3.5.0",
"name": "probos",
"version": "3.5.0"
},
{
"build": "121.1666598992258.commit",
"name": "rqtsentry",
"version": "3.10.0"
},
{
"build": "45.1666597836648.commit",
"name": "rqtnetsentry",
"version": "3.10.0"
},
{
"build": "",
"name": "installer",
"version": "3.10.1"
}
],
"connected": true,
"cpuDescr": "Intel(R) Xeon(R) Platinum 8260 CPU @ 2.40GHz",
"cpuVendor": 1,
"disconnectionReason": 0,
"domain": "americas.cloudpaksecurity.com",
"groups": [
{
"description": "Latin America Hive",
"id": "839608851933167623",
"name": "Latin America"
}
],
"hvStatus": 19,
"id": "876174682842202112",
"isDomainController": true,
"isServer": true,
"isVirtualMachine": false,
"isolated": false,
"isolationStatus": "DEISOLATED",
"isolationStatusFailure": null,
"kernel": "10.0",
"lastSeenAt": "2023-08-01T07:18:21.342Z",
"localAddr": "52.118.133.13",
"machineId": "857d21c8a80297fb0078cdc036b290b61cb4eec5c1889eab4c7ae3daeeeaa655",
"macs": [
"06:c3:1d:18:2c:3a",
"06:d7:b5:4f:18:0e"
],
"name": "ADDAL10-01",
"os": "Windows Server 2019 Standard",
"osType": 1,
"registrationTime": "2022-06-17T20:05:22.942Z",
"sessionEnd": "2023-08-01T07:23:21.342Z",
"sessionStart": "2023-04-25T09:11:13.842Z",
"state": 1,
"tags": [
"dc"
]
},
"endpointId": "876174682842202112",
"endpointState": {
"arch": 2,
"componentsVersions": [
{
"build": "27.1668701555901.commit",
"name": "keeper",
"version": "3.10.1"
},
{
"build": "3.5.0",
"name": "probos",
"version": "3.5.0"
},
{
"build": "121.1666598992258.commit",
"name": "rqtsentry",
"version": "3.10.0"
},
{
"build": "45.1666597836648.commit",
"name": "rqtnetsentry",
"version": "3.10.0"
},
{
"build": "",
"name": "installer",
"version": "3.10.1"
}
],
"cpuDescr": "Intel(R) Xeon(R) Platinum 8260 CPU @ 2.40GHz",
"cpuVendor": 1,
"domain": "americas.cloudpaksecurity.com",
"endpointVersion": "3.10.1",
"groups": [
{
"description": "Latin America Hive",
"id": "839608851933167623",
"name": "Latin America"
}
],
"hvStatus": 19,
"isolated": false,
"kernel": "10.0",
"localAddr": "52.118.133.13",
"macs": [
"06:c3:1d:18:2c:3a",
"06:d7:b5:4f:18:0e"
],
"name": "ADDAL10-01",
"os": "Windows Server 2019 Standard",
"osType": 1,
"tags": [
"dc"
]
},
"happenedAt": "2023-07-25T10:22:16.669Z",
"id": "1022070806768779266",
"impact": 88,
"lastChangedAt": "2023-07-27T00:01:03.899Z",
"localId": "1022070249672935426",
"notes": "\nIBM SOAR 25/07/2023 10:25:05\nNone\n\n[SOAR Case - 2825](https://9.30.229.231:443/#incidents/2825)\nIBM SOAR 25/07/2023 18:25:21\nNone\n\n[SOAR Case - 2151](https://9.30.211.113:443/#incidents/2151)\nIBM SOAR 25/07/2023 10:25:32\n\nIBM SOAR 25/07/2023 10:22:23\nNone\n\n[SOAR Case - 17384](https://169.44.147.200:443/#incidents/17384)\n\n[SOAR Case - 2828](https://9.30.229.231:443/#incidents/2828)\nIBM SOAR 27/07/2023 00:01:03\n\nIBM SOAR 25/07/2023 10:25:05\nNone\n\n[SOAR Case - 2825](https://9.30.229.231:443/#incidents/2825)\nIBM SOAR 25/07/2023 18:25:21\nNone\n\n[SOAR Case - 2151](https://9.30.211.113:443/#incidents/2151)\nIBM SOAR 25/07/2023 10:25:32\n\nIBM SOAR 25/07/2023 10:22:23\nNone\n\n[SOAR Case - 17384](https://169.44.147.200:443/#incidents/17384)\n\n[SOAR Case - 2828](https://9.30.229.231:443/#incidents/2828)\n\n[SOAR Case - 2943](https://9.30.24.113:443/#incidents/2943)",
"receivedAt": "2023-07-25T10:24:29.491Z",
"severity": "medium",
"tags": [],
"terminationReason": 1,
"title": "Policy hit: johns policy 2007",
"totalEventCount": 6,
"triggerCondition": 6,
"triggerEvents": [
{
"category": "policies",
"data": {
"_t": "r",
"matched": [
{
"groups": [],
"matcher": {
"alg": 1,
"hash": "de96a6e69944335375dc1ac238336066889d9ffc7d73628ef4fe1b1b160ab32c",
"id": "1020293408461168646",
"type": 2
},
"policyDescription": "test",
"policyId": "1020293408461160452",
"policyTitle": "johns policy 2007",
"scope": "global",
"versionId": "1020293408461164549"
}
]
},
"endpointId": "876174682842202112",
"eventType": 28,
"happenedAt": "2023-07-25T10:22:16.652Z",
"happenedAt_ts": 1690280536000,
"id": "1022070807062380545",
"localId": "1022070249601636353",
"manuallyAdded": false,
"process": {
"endpointId": "876174682842202112",
"id": "876174682842202112:8944:1690280536643",
"logonId": "0x3e7",
"noGui": false,
"parentId": "876174682842202112:4780:1690280518291",
"pid": 8944,
"ppid": 4780,
"privilegeLevel": "SYSTEM",
"program": {
"arch": "x64",
"certInfo": {
"expired": false,
"issuer": "Microsoft Windows Production PCA 2011",
"signer": "Microsoft Windows",
"trusted": true
},
"filename": "powershell.exe",
"fsName": "powershell.exe",
"md5": "7353f60b1739074eb17c5f4dddefe239",
"path": "c:\\windows\\system32\\windowspowershell\\v1.0\\powershell.exe",
"sha1": "6cbce4a295c163791b60fc23d285e6d84f28ee4c",
"sha256": "de96a6e69944335375dc1ac238336066889d9ffc7d73628ef4fe1b1b160ab32c",
"size": 448000
},
"pstartTime": "2023-07-25T10:21:58.291Z",
"startTime": "2023-07-25T10:22:16.643Z",
"user": "NT AUTHORITY\\SYSTEM",
"userSID": "S-1-5-18"
},
"receivedAt": "2023-07-25T10:24:29.561Z",
"relevance": 88,
"severity": "medium",
"trigger": true
}
]
},
"inputs": {
"reaqta_alert_id": "1022070806768779266",
"reaqta_hive": "rhiveam"
},
"metrics": {
"execution_time_ms": 1786,
"host": "local",
"package": "fn-reaqta",
"package_version": "1.1.0",
"timestamp": "2023-08-01 15:18:53",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.reaqta_alert_id = incident.properties.reaqta_id
inputs.reaqta_hive = incident.properties.reaqta_hive
Example Function Post Process Script:
TRIGGERCONDITION_LOOKUP = {
0: "Code Injection",
1: "Process Impersonated",
2: "Signature Forged",
3: "Incident Correlated",
4: "DLL Sideloaded",
5: "Suspicious Script Executed",
6: "Policies Triggered",
7: "Anomalous Behaviour Detected",
8: "Token Stolen",
9: "Ransomware Behavior Detected",
10: "Privilege Escalated",
11: "External Trigger",
12: "Detection Strategy",
13: "Antimalware Detection"
}
results = playbook.functions.results.reaqta_get_alert_information_result
if not results.success:
incident.addNote("ReaQta: Get Alert Information failed: {}".format(results.reason))
else:
content = results.content
impact_sv = incident.properties.reaqta_impact
incident.severity_code = "Low" if content.get('severity') in ['safe', 'low'] else content.get('severity', 'low').title()
incident.properties.reaqta_impact = content.get("impact")
if (impact_sv and impact_sv != incident.properties.reaqta_impact):
incident.addNote("ReaQta impact changed from '{}' to '{}'. Case severity: {}".format(impact_sv, incident.properties.reaqta_impact, incident.severity_code))
incident.properties.reaqta_endpoint_id = content.get("endpointId")
incident.properties.reaqta_trigger_condition = TRIGGERCONDITION_LOOKUP.get(content.get("triggerCondition"))
endpoint = content.get("endpoint", {})
incident.properties.reaqta_tags = ", ".join(content.get("tags", []))
incident.properties.reaqta_groups = ", ".join([ group.get("name") for group in endpoint.get("groups", []) ])
incident.properties.reaqta_machine_info = "Machine Name: {}\nOS: {}\nDomain: {}\nCPU: {}"\
.format(endpoint.get('name'),
endpoint.get('os'),
endpoint.get('domain'),
endpoint.get('cpuDescr'))
# populate datatable with trigger events
for event in content.get('triggerEvents', []):
row = incident.addRow('reaqta_trigger_events')
row['happened_at'] = event.get('happenedAt_ts')
row['category'] = event.get('category')
row['relevance'] = event.get('relevance')
row['severity'] = event.get('severity')
process = event.get('process', {})
program = process.get('program', {})
if program:
row['process_pid'] = process.get('pid')
row['program_path'] = program.get('path')
row['sha256_hash'] = program.get('sha256')
if event.get('category') == "etw" and event.get('data'):
data = event.get('data')
row['windows_event_account'] = "{}\\{}".format(data.get('etwTargetDomainName'), data.get('etwTargetUserName'))
row['windows_event_workstation'] = data.get('etwWorkstationName')
row['windows_event_description'] = data.get('etwEventDescription')
row['windows_event_ipport'] = "{}/{}".format(data.get('etwIpAddress'), data.get('etwIpPort'))
if event.get('category') == "policies" and event.get('data'):
data = event.get('data')
row['policy_match'] = data.get('matched', [])[0]['policyTitle']
# create artifacts from the trigger event
if program:
incident.addArtifact("Malware SHA-256 Hash", program.get('sha256'), "")
incident.addArtifact("File Path", program.get('path'), "")
incident.addArtifact("File Name", program.get('filename'), "")
if process:
incident.addArtifact("User Account", process.get('user'), "")
# create artifacts from endpoint
endpoint_name = endpoint.get("name")
incident.addArtifact("IP Address", endpoint.get("localAddr"), "Endpoint: {}".format(endpoint_name))
incident.addArtifact("System Name", endpoint_name, "")
Function - QRadar EDR: Get Endpoint Status¶
Get the current status of an endpoint

Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
- |
|
|
No |
|
Label used to identify which ReaQta hive this alert is associated with |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"agentVersion": "3.10.1",
"arch": 2,
"avInstalled": false,
"componentsVersions": [
{
"build": "27.1668701555901.commit",
"name": "keeper",
"version": "3.10.1"
},
{
"build": "3.5.0",
"name": "probos",
"version": "3.5.0"
},
{
"build": "121.1666598992258.commit",
"name": "rqtsentry",
"version": "3.10.0"
},
{
"build": "45.1666597836648.commit",
"name": "rqtnetsentry",
"version": "3.10.0"
},
{
"build": "",
"name": "installer",
"version": "3.10.1"
}
],
"connected": true,
"cpuDescr": "Intel(R) Xeon(R) Platinum 8260 CPU @ 2.40GHz",
"cpuVendor": 1,
"disconnectionReason": 0,
"domain": "infosec.local",
"groups": [
{
"id": "939525795968188423",
"name": "Servers",
"parentGroupId": "817450822869712903"
},
{
"id": "817450822869712903",
"name": "Product Team"
}
],
"hvStatus": 19,
"id": "836686917654282240",
"isDomainController": true,
"isServer": true,
"isVirtualMachine": true,
"isolated": true,
"isolationStatus": "ISOLATED",
"isolationStatusFailure": null,
"kernel": "10.0",
"lastSeenAt": "2023-08-07T06:24:44.472Z",
"localAddr": "172.16.60.189",
"machineId": "d67dc4211cb83f014c33af976208cc601e35abf251e405e8841e1cb449a48b0e",
"macs": [
"00:0c:29:8f:93:ee"
],
"name": "ACTIVEDIRECTORY",
"os": "Windows Server 2019 Standard",
"osType": 1,
"registrationTime": "2022-02-28T20:55:06.087Z",
"sessionEnd": "2023-08-07T06:29:44.472Z",
"sessionStart": "2023-06-22T09:11:49.712Z",
"state": 1,
"tags": [
"vm",
"pci",
"production",
"dc"
]
},
"inputs": {
"reaqta_endpoint_id": "836686917654282240",
"reaqta_hive": "rhiveam"
},
"metrics": {
"execution_time_ms": 1008,
"host": "local",
"package": "fn-reaqta",
"package_version": "1.1.0",
"timestamp": "2023-08-07 14:25:34",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.reaqta_endpoint_id = incident.properties.reaqta_endpoint_id
inputs.reaqta_hive = incident.properties.reaqta_hive
Example Function Post Process Script:
DISCONNECTION_LOOKUP = {
0: "Session timeout",
1: "Deregistration"
}
results = playbook.functions.results.reaqta_get_endpoint_status_result
if results.success:
endpoint = results.content
msg = """ReaQta Get Endpoint Status:
ID: {}
Endpoint: {}
Agent version: {}
Last Seen At: {}
Connected: {}
Isolated: {}
Disconnection Reason: {}
Tags: {}
Groups: {}
""".format(endpoint.get("id"),
endpoint.get("name"),
endpoint.get("agentVersion"),
endpoint.get("lastSeenAt"),
endpoint.get("connected"),
endpoint.get("isolated"),
DISCONNECTION_LOOKUP.get(endpoint.get("disconnectionReason")),
", ".join(endpoint.get("tags")),
", ".join([group.get("name") for group in endpoint.get("groups", [])])
)
incident.addNote(helper.createPlainText(msg))
else:
incident.addNote(u"ReaQta Get Endpoint Status failed: {}".format(results.reason))
Function - QRadar EDR: Get Processes¶
Get active processes from a given endpoint

Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
- |
|
|
No |
|
Select only processes associated with an incident |
|
|
No |
|
Label used to identify which ReaQta hive this alert is associated with |
|
|
No |
|
Select only processes which are suspended |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": [
{
"hasIncident": false,
"pid": 0,
"ppid": 0,
"processName": "[System Process]",
"startTime": 0,
"suspended": false
},
{
"hasIncident": false,
"pid": 4,
"ppid": 0,
"privilegeLevel": "SYSTEM",
"processName": "System",
"startTime": 1689857459354,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 104,
"ppid": 4,
"privilegeLevel": "SYSTEM",
"processName": "Registry",
"startTime": 1689857454562,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 316,
"ppid": 4,
"privilegeLevel": "SYSTEM",
"processName": "smss.exe",
"programPath": "C:\\Windows\\System32\\smss.exe",
"startTime": 1689857459360,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 428,
"ppid": 416,
"privilegeLevel": "SYSTEM",
"processName": "csrss.exe",
"programPath": "C:\\Windows\\System32\\csrss.exe",
"startTime": 1689857462103,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 532,
"ppid": 416,
"privilegeLevel": "SYSTEM",
"processName": "wininit.exe",
"programPath": "C:\\Windows\\System32\\wininit.exe",
"startTime": 1689857462246,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 540,
"ppid": 524,
"privilegeLevel": "SYSTEM",
"processName": "csrss.exe",
"programPath": "C:\\Windows\\System32\\csrss.exe",
"startTime": 1689857462248,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 600,
"ppid": 524,
"privilegeLevel": "SYSTEM",
"processName": "winlogon.exe",
"programPath": "C:\\Windows\\System32\\winlogon.exe",
"startTime": 1689857462267,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 676,
"ppid": 532,
"privilegeLevel": "SYSTEM",
"processName": "services.exe",
"programPath": "C:\\Windows\\System32\\services.exe",
"startTime": 1689857462392,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 716,
"ppid": 532,
"privilegeLevel": "SYSTEM",
"processName": "lsass.exe",
"programPath": "C:\\Windows\\System32\\lsass.exe",
"startTime": 1689857462441,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 928,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857463992,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 952,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464035,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1000,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464115,
"suspended": false,
"user": "NT AUTHORITY\\NETWORK SERVICE"
},
{
"hasIncident": false,
"pid": 288,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464133,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 528,
"ppid": 600,
"privilegeLevel": "SYSTEM",
"processName": "LogonUI.exe",
"programPath": "C:\\Windows\\System32\\LogonUI.exe",
"startTime": 1689857464195,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 788,
"ppid": 600,
"privilegeLevel": "SYSTEM",
"processName": "dwm.exe",
"programPath": "C:\\Windows\\System32\\dwm.exe",
"startTime": 1689857464228,
"suspended": false,
"user": "Window Manager\\DWM-1"
},
{
"hasIncident": false,
"pid": 1020,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464259,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 432,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464259,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 524,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464259,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 1104,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464267,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1120,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464268,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 1152,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464271,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 1220,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464280,
"suspended": false,
"user": "NT AUTHORITY\\NETWORK SERVICE"
},
{
"hasIncident": false,
"pid": 1396,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464309,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 1416,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464312,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 1492,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464343,
"suspended": false,
"user": "NT AUTHORITY\\NETWORK SERVICE"
},
{
"hasIncident": false,
"pid": 1548,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464376,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1564,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464379,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 1608,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464387,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1616,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464387,
"suspended": false,
"user": "NT AUTHORITY\\NETWORK SERVICE"
},
{
"hasIncident": false,
"pid": 1624,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464388,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 1680,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464398,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1756,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464411,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1820,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464425,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1900,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464449,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1908,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464449,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1932,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464451,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 2028,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464523,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 2116,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464552,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 2188,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464579,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 2248,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464599,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 2288,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464610,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 2344,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857464635,
"suspended": false,
"user": "NT AUTHORITY\\NETWORK SERVICE"
},
{
"hasIncident": false,
"pid": 2808,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857466649,
"suspended": false,
"user": "NT AUTHORITY\\NETWORK SERVICE"
},
{
"hasIncident": false,
"pid": 2984,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857473991,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 2668,
"ppid": 600,
"privilegeLevel": "LOW",
"processName": "fontdrvhost.exe",
"programPath": "C:\\Windows\\System32\\fontdrvhost.exe",
"startTime": 1689857485108,
"suspended": false,
"user": "Font Driver Host\\UMFD-1"
},
{
"hasIncident": false,
"pid": 2124,
"ppid": 532,
"privilegeLevel": "LOW",
"processName": "fontdrvhost.exe",
"programPath": "C:\\Windows\\System32\\fontdrvhost.exe",
"startTime": 1689857485108,
"suspended": false,
"user": "Font Driver Host\\UMFD-0"
},
{
"hasIncident": false,
"pid": 2912,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "spoolsv.exe",
"programPath": "C:\\Windows\\System32\\spoolsv.exe",
"startTime": 1689857485129,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1800,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857485156,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 2652,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857485156,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 2952,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "Microsoft.ActiveDirectory.WebServices.exe",
"programPath": "C:\\Windows\\ADWS\\Microsoft.ActiveDirectory.WebServices.exe",
"startTime": 1689857485158,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 3092,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857485164,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 3100,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857485164,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 3108,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857485164,
"suspended": false,
"user": "NT AUTHORITY\\NETWORK SERVICE"
},
{
"hasIncident": false,
"pid": 3116,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "ismserv.exe",
"programPath": "C:\\Windows\\System32\\ismserv.exe",
"startTime": 1689857485165,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 3124,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "dfsrs.exe",
"programPath": "C:\\Windows\\System32\\dfsrs.exe",
"startTime": 1689857485166,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 3136,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "dns.exe",
"programPath": "C:\\Windows\\System32\\dns.exe",
"startTime": 1689857485168,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 3148,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857485170,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 3156,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "vm3dservice.exe",
"programPath": "C:\\Windows\\System32\\vm3dservice.exe",
"startTime": 1689857485175,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 3164,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "vmtoolsd.exe",
"programPath": "C:\\Program Files\\VMware\\VMware Tools\\vmtoolsd.exe",
"startTime": 1689857485176,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 3176,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "MsMpEng.exe",
"programPath": "C:\\ProgramData\\Microsoft\\Windows Defender\\Platform\\4.18.23050.5-0\\MsMpEng.exe",
"startTime": 1689857485181,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 3184,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "VGAuthService.exe",
"programPath": "C:\\Program Files\\VMware\\VMware Tools\\VMware VGAuth\\VGAuthService.exe",
"startTime": 1689857485184,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 3396,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "dfssvc.exe",
"programPath": "C:\\Windows\\System32\\dfssvc.exe",
"startTime": 1689857485250,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 3500,
"ppid": 3156,
"privilegeLevel": "SYSTEM",
"processName": "vm3dservice.exe",
"programPath": "C:\\Windows\\System32\\vm3dservice.exe",
"startTime": 1689857485278,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 3672,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857485381,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 4080,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "vds.exe",
"programPath": "C:\\Windows\\System32\\vds.exe",
"startTime": 1689857485735,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 4104,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "dllhost.exe",
"programPath": "C:\\Windows\\System32\\dllhost.exe",
"startTime": 1689857485768,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 4116,
"ppid": 952,
"privilegeLevel": "SYSTEM",
"processName": "WmiPrvSE.exe",
"programPath": "C:\\Windows\\System32\\wbem\\WmiPrvSE.exe",
"startTime": 1689857485773,
"suspended": false,
"user": "NT AUTHORITY\\NETWORK SERVICE"
},
{
"hasIncident": false,
"pid": 4868,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "msdtc.exe",
"programPath": "C:\\Windows\\System32\\msdtc.exe",
"startTime": 1689857486284,
"suspended": false,
"user": "NT AUTHORITY\\NETWORK SERVICE"
},
{
"hasIncident": false,
"pid": 5088,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857486681,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 4036,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857486795,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 5568,
"ppid": 3200,
"privilegeLevel": "SYSTEM",
"processName": "keeper.exe",
"programPath": "C:\\Program Files\\ReaQta\\keeper.exe",
"startTime": 1689857489492,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 5684,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "NisSrv.exe",
"programPath": "C:\\ProgramData\\Microsoft\\Windows Defender\\Platform\\4.18.23050.5-0\\NisSrv.exe",
"startTime": 1689857491007,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 5140,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857606087,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 1084,
"ppid": 3296,
"privilegeLevel": "SYSTEM",
"processName": "GoogleCrashHandler.exe",
"programPath": "C:\\Program Files (x86)\\Google\\Update\\1.3.36.272\\GoogleCrashHandler.exe",
"startTime": 1689857606810,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 672,
"ppid": 3296,
"privilegeLevel": "SYSTEM",
"processName": "GoogleCrashHandler64.exe",
"programPath": "C:\\Program Files (x86)\\Google\\Update\\1.3.36.272\\GoogleCrashHandler64.exe",
"startTime": 1689857606921,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1356,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857606989,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 356,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857611856,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1640,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689857612336,
"suspended": false,
"user": "NT AUTHORITY\\LOCAL SERVICE"
},
{
"hasIncident": false,
"pid": 5184,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689859046435,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 1716,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "svchost.exe",
"programPath": "C:\\Windows\\System32\\svchost.exe",
"startTime": 1689943866540,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
},
{
"hasIncident": false,
"pid": 2680,
"ppid": 676,
"privilegeLevel": "SYSTEM",
"processName": "SecurityHealthService.exe",
"programPath": "C:\\Windows\\System32\\SecurityHealthService.exe",
"startTime": 1690339871083,
"suspended": false,
"user": "NT AUTHORITY\\SYSTEM"
}
],
"inputs": {
"reaqta_endpoint_id": "836686917654282240",
"reaqta_has_incident": null,
"reaqta_hive": "rhiveam",
"reaqta_suspended": null
},
"metrics": {
"execution_time_ms": 1889,
"host": "local",
"package": "fn-reaqta",
"package_version": "1.1.0",
"timestamp": "2023-08-01 15:49:17",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.reaqta_endpoint_id = incident.properties.reaqta_endpoint_id
inputs.reaqta_has_incident = playbook.inputs.reaqta_has_incident
inputs.reaqta_suspended = playbook.inputs.reaqta_suspended
inputs.reaqta_hive = incident.properties.reaqta_hive
Example Function Post Process Script:
from datetime import datetime
now = datetime.now()
def bool_to_str(value):
return 'True' if value else 'False'
results = playbook.functions.results.reaqta_get_processes_result
if results.success:
if isinstance(results.content, list):
if results.content:
for process in results.content:
row = incident.addRow("reaqta_process_list")
row['report_date'] = now
row["pid"] = process.get("pid")
row["process_name"] = process.get("processName")
row["process_path"] = process.get("programPath")
row["privilege_level"] = process.get("privilegeLevel")
row["user"] = process.get("user")
row["has_incident"] = process.get("hasIncident")
row["suspended"] = process.get("suspended")
row["start_time"] = process.get("startTime")
process_num = len(results.content)
incident.addNote("Number of processes queried: {}\nQuery Inputs: \nReaQta End Point id: {}, Has Incident: {}, Suspended: {}, ReaQta Hive: {}\nReaQta Process List Data table updated!\n".format(process_num,incident.properties.reaqta_endpoint_id, playbook.inputs.reaqta_has_incident, playbook.inputs.reaqta_suspended, incident.properties.reaqta_hive))
else:
incident.addNote(u"ReaQta Get Processes - no processes found for input parameters: Has Incident: {}, Suspended: {}".\
format(bool_to_str(results.inputs.get("reaqta_has_incident")), bool_to_str(results.inputs.get("reaqta_suspended"))))
else:
incident.addNote(u"ReaQta Get Processes unsuccessful: {}".format(results.content.get('message')))
else:
incident.addNote(u"ReaQta Get Processes failed: {}".format(results.reason))
Function - QRadar EDR: Isolate Machine¶
Isolate a ReaQta controlled machine based on it’s endpoint ID

Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
- |
|
|
No |
|
Label used to identify which ReaQta hive this alert is associated with |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": {
"success": true
},
"inputs": {
"reaqta_endpoint_id": "836686917654282240",
"reaqta_hive": "rhiveam"
},
"metrics": {
"execution_time_ms": 443,
"host": "local",
"package": "fn-reaqta",
"package_version": "1.1.0",
"timestamp": "2023-08-07 14:32:03",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.reaqta_endpoint_id = incident.properties.reaqta_endpoint_id
inputs.reaqta_hive = incident.properties.reaqta_hive
Example Function Post Process Script:
results = playbook.functions.results.reaqta_isolate_machine_result
if results.success and results.content.get('success'):
msg = "Endpoint Machine Isolated"
elif results.reason:
msg = u"ReaQta Isolate Machine failed: {}".format(results.reason)
else:
msg = u"ReaQta Isolate Machine failed: {}".format(results.content.get('message'))
incident.addNote(msg)
Function - QRadar EDR: Kill Process¶
Kill a process on a machine by the process PID

Inputs:
Name |
Type |
Required |
Example |
Tooltip |
|---|---|---|---|---|
|
|
Yes |
|
- |
|
|
No |
|
Label used to identify which ReaQta hive this alert is associated with |
|
|
Yes |
|
- |
|
|
Yes |
|
- |
Outputs:
NOTE: This example might be in JSON format, but
resultsis a Python Dictionary on the SOAR platform.
results = {
"content": [
{
"error": "Process not found",
"errorCode": -1,
"killed": false,
"pid": 428,
"startTime": 1689857462103
}
],
"inputs": {
"reaqta_endpoint_id": "836686917654282240",
"reaqta_hive": "rhiveam",
"reaqta_process_pid": 428,
"reaqta_starttime": 1689857462103
},
"metrics": {
"execution_time_ms": 971,
"host": "local",
"package": "fn-reaqta",
"package_version": "1.1.0",
"timestamp": "2023-08-07 14:26:49",
"version": "1.0"
},
"raw": null,
"reason": null,
"success": true,
"version": 2.0
}
Example Function Input Script:
inputs.reaqta_endpoint_id = incident.properties.reaqta_endpoint_id
inputs.reaqta_process_pid = row['pid']
inputs.reaqta_starttime = row['start_time']
inputs.reaqta_hive = incident.properties.reaqta_hive
Example Function Post Process Script:
from datetime import datetime
now = datetime.now()
results = playbook.functions.results.reaqta_kill_process_result
if results.success:
for process in results.content:
row['report_date'] = now
if process.get('killed'):
row['status'] = 'killed'
msg = u"Process: {} ({}) killed".format(row['process_name'], row['pid'])
else:
row['status'] = process.get('error')
msg = u"Process: {} ({}) kill failed: {}".format(row['process_name'], row['pid'], process.get('error'))
incident.addNote(msg)
break;
else:
incident.addNote(u"ReaQta Kill Process failed: {}".format(results.reason))
Data Table - QRadar EDR Process List¶
API Name:¶
reaqta_process_list
Columns:¶
Column Name |
API Access Name |
Type |
Tooltip |
|---|---|---|---|
PID |
|
|
- |
Privilege Level |
|
|
- |
Process Path |
|
|
- |
Process Suspended |
|
|
- |
Program Name |
|
|
- |
Related to Alert |
|
|
- |
Report Date |
|
|
- |
Start Time |
|
|
- |
Status |
|
|
- |
User |
|
|
- |
Data Table - QRadar EDR Trigger Events¶
API Name:¶
reaqta_trigger_events
Columns:¶
Column Name |
API Access Name |
Type |
Tooltip |
|---|---|---|---|
Category |
|
|
- |
Happened At |
|
|
- |
PID |
|
|
- |
Policy Match |
|
|
- |
Program Path |
|
|
- |
Relevance |
|
|
- |
Severity |
|
|
- |
SHA256 Hash |
|
|
- |
Windows Event Account |
|
|
- |
Windows Event Description |
|
|
- |
Windows Event IP/Port |
|
|
- |
Windows Event Workstation |
|
|
- |
Custom Fields¶
Label |
API Access Name |
Type |
Prefix |
Placeholder |
Tooltip |
|---|---|---|---|---|---|
QRadar EDR Alert Link |
|
|
|
- |
- |
QRadar EDR Endpoint ID |
|
|
|
- |
- |
QRadar EDR Endpoint Link |
|
|
|
- |
- |
QRadar EDR Groups |
|
|
|
- |
- |
QRadar EDR Hive |
|
|
|
- |
ReaQta hive reference when multiple hives are present |
QRadar EDR Alert ID |
|
|
|
- |
- |
QRadar EDR Impact |
|
|
|
- |
- |
QRadar EDR Machine Info |
|
|
|
- |
- |
QRadar EDR Tags |
|
|
|
- |
- |
QRadar EDR Trigger Condition |
|
|
|
- |
- |
Playbooks¶
Playbook Name |
Description |
Activation Type |
Object |
Status |
Condition |
|---|---|---|---|---|---|
QRadar EDR: Close Alert (PB) |
Close the ReaQta Alert |
Automatic |
incident |
|
|
QRadar EDR: Create Artifact from Process Path (PB) |
Create an artifact from a ReaQta Endpoint process file. |
Manual |
reaqta_process_list |
|
|
QRadar EDR: Create Artifact from Trigger Event (PB) |
None |
Automatic |
reaqta_trigger_events |
|
|
QRadar EDR: Create Attachment from Process List (PB) |
Attach a file from an endpoint’s process list |
Manual |
reaqta_process_list |
|
|
QRadar EDR: Create Attachment from Triggered Event (PB) |
Attach a file from an endpoint. |
Manual |
reaqta_trigger_events |
|
|
QRadar EDR: Create Note (PB) |
Add a note from SOAR to ReaQta |
Automatic |
note |
|
|
QRadar EDR: Create Policy from Artifact (PB) |
Create a blocking policy from a SHA256 hash |
Manual |
artifact |
|
|
QRadar EDR: Create Policy on Triggered Event (PB) |
Create an alert trigger policy based on a file hash |
Manual |
reaqta_trigger_events |
|
|
QRadar EDR: Deisolate Endpoint (PB) |
De-isolate the endpoint machine from the network |
Manual |
incident |
|
|
QRadar EDR: Get Alert Information (PB) |
Get alert information and populate the custom fields and datatables |
Automatic |
incident |
|
|
QRadar EDR: Get Endpoint Status (PB) |
Get the current status of a ReaQta Endpoint |
Manual |
incident |
|
|
QRadar EDR: Get Processes (PB) |
Get the running processes on a given machine |
Manual |
incident |
|
|
QRadar EDR: Isolate Endpoint (PB) |
Isolate the endpoint machine from the network |
Manual |
incident |
|
|
QRadar EDR: Kill Process (PB) |
Get the running processes on a given machine |
Manual |
reaqta_process_list |
|
|
QRadar EDR: Refresh Alert Information (PB) |
Refresh alert information and populate the custom fields and datatables |
Manual |
incident |
|
|
Troubleshooting & Support¶
Refer to the documentation listed in the Requirements section for troubleshooting information.
For Support¶
This is an IBM supported app. Please search ibm.com/mysupport for assistance.